-
CENTRES
Progammes & Centres
Location
The Scorpene leak can be the first instance of information about India’s strategic assets being successfully extracted through digital networks.

Defence Minister Manohar Parikkar has suggested that sensitive details of the Scorpene submarine, slated to join the Indian Navy’s fleet next year, were “hacked” and consequently leaked to third parties. If he is right, this would be the first publicly recorded instance of information about India’s strategic assets being successfully extracted through digital networks. Parikkar is not the only high-level official to imply that the Scorpene files have been hacked. Australian Prime Minister Malcolm Turnbull hinted that the leak is a “clear reminder” that cyber security is of paramount importance. Australia also plans to induct the Scorpene into its Navy.
An alternative theory, been offered by The Australian — the news outlet that broke news of the leak — is that the data was “removed from France” by a former French navy officer, then changing hands in Asia. The possibility that this was the action of a disgruntled officer or an employee selling commercial secrets cannot be ruled out. Simply “removing” data from the servers of DCNS — the French defence conglomerate that designed Scorpene — is however, easier said than done. Companies like DCNS go extraordinary lengths to protect the sensitive data they handle. There are usually three levels of protection that militaries and private defence agencies put in place to prevent data leaks or cyber espionage:
It is extremely difficult, but not impossible, for any individual to bypass such restrictions and physically extract data from DCNS servers. From what we’ve seen of the leaked data, it essentially comprises scanned copies of printed documents, and PDF files. There is no doubt these documents have been electronically obtained. If the files themselves were circulated through a data disk, it is puzzling why a screenshot of the folder containing the documents would also appear in the trove of leaks.
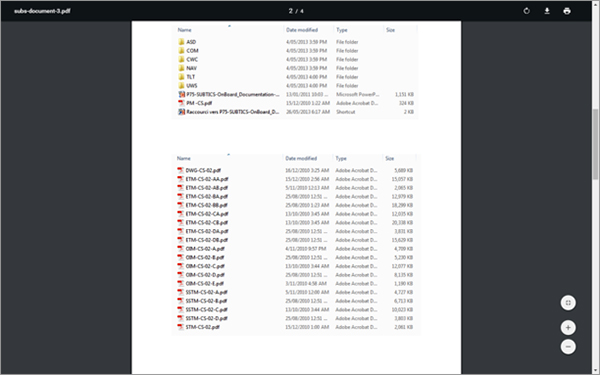
It is conceivable that none of the safeguards listed here were in place five years ago, when the leak is alleged to have occurred. That said, Thales, the French private company that holds a minority stake in DCNS, is among the foremost providers of cyber security in the world. (As the joke goes, companies like Thales and Airbus became experts at cybersecurity because they learnt to fend off their own networks from espionage while doing business in China).
The jury is out for now, but it will become clear in the days ahead whether the Scorpene files have been hacked. Cyber-espionage usually leaves an indelible trail of electronic crumbs, and it is only a matter of time before investigators stumble upon them. If these files have indeed been hacked, the investigation may reveal:
India’s armed forces and computer emergency response teams are prepared for these contingencies, which is why it would be surprising to learn that the leak has happened on the Indian side. Civilian entities, especially companies, on the other hand, do not have the luxury of “air-gapping” their networks (i.e., insulating them from the general internet). Whether or not the Scorpene files were leaked through an act of cyber espionage, the epsiode is a reminder to India’s defence agencies that their increased involvement with the private sector for the co-development of weapons systems will require additional layers of digital security to be the put in place.
The views expressed above belong to the author(s). ORF research and analyses now available on Telegram! Click here to access our curated content — blogs, longforms and interviews.

Hildegunn Kyvik Nords Senior Associate Council on Economic Policies Zurich and rebro University
Read More +