
Earlier this month the “
strongest public response to a cyberattack” was witnessed when Albania severed diplomatic relations with Iran over its role in the devastating cyberattacks against Albania’s government infrastructure. This cascading incident highlights the vast differences in nation-state capabilities and defences within cyberspace, and how offensive cyber operations can devastate those nations caught in the middle.
On 17 July 2022,
Albania was hit by a series of cyberattacks that targeted public services and government websites. The attack, claimed by ‘
HomeLand Justice’ employed new family ransomware malware, ROADSWEEP, and a new variant of a wiper malware, ZEROCLEAR. Since Albania is a NATO member, and these attacks are happening during Russia’s ongoing invasion of Ukraine, the
local media speculated that Russia was the culprit.
This speculation faded quickly after a US cyber threat intelligence firm, Mandiant,
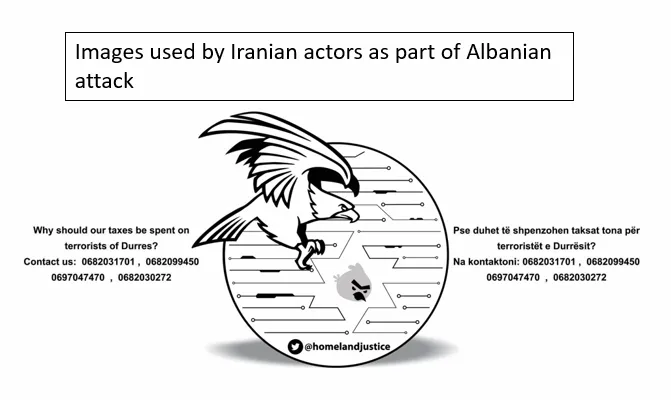
attributed the cyberattack and the ‘HomeLand Justice’ group to Iran. Their analysis was aided by the imagery used on the ‘HomeLand Justice’ group’s Telegram channel. Iran had posted a banner image which depicted an eagle swooping down on a smaller bird within the Star of David.
 Source: Mandiant
Source: Mandiant
The smaller bird—a character from the Angry Bird franchise—seemed innocuous but provided analysts a clear link to Iran. John Hultquist, Vice President, Mandiant Threat Intelligence, explained that the smaller bird had been claimed by ‘
Predatory Sparrow’, a threat actor that has conducted offensive cyber operations against Iran.
 Source: Mandiant
Source: Mandiant
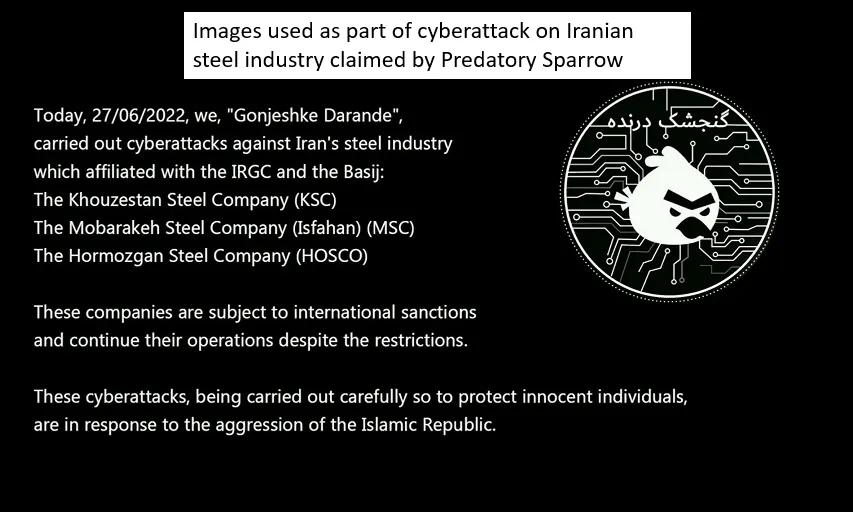
In fact, since July 2021, the ‘Predatory Sparrow’ threat actor has been conducting
measured, destructive, and disruptive cyber operations against Iran. Their offensive cyber operations
disrupted rail services,
cut off fuel distribution, and even
destroyed a steel plant affiliated with the Iranian Revolutionary Guard Corps.
There’s no clear evidence to suggest that Albania’s government had a role in ‘Predatory Sparrow’s operations, yet Iran deemed them a fair target in responding against ‘Predatory Sparrow’s actions. The prevailing theory, supported by a
new report from Microsoft, suggests that ‘Predatory Sparrow’ is linked to the exiled Iranian opposition group, the Mujahedin-e-Khalq (MeK) which operates out of Albania and
Israel. This is further supported by
terrorist threats that cancelled a planned MeK conference in Albania.
Given ‘Predatory Sparrow’s year-long destructive cybercampaign, Iran was justifiably itching to respond. Albania, regarded by Iran as a
“safe haven” for the MeK, is more of an ‘unwitting conspirator’ than a knowing participant in this ongoing cyber conflict. Albania is considered to be the “
fifth largest source of cybercrime in Europe”, which only recently took steps to develop a cybercrime centre, and received
18 million euros in November 2021 to establish a cyber military force. After a massive leak of
citizen data in December 2021, Albania brought in
US firms to bolster its cyber defences.
Even though Albania lacked proper cyber defences, it is a member of NATO. The military alliance has been reinvigorated, following Russia’s invasion of Ukraine and in February 2022, it reaffirmed that a cyberattack on a NATO member state
could trigger Article 5—the alliance’s collective defence clause, last activated by the US after the 9/11 terror attacks. However, NATO has since declined to clarify what threshold a significant cyberattack (or “
an accumulation of smaller ones”) would need to cross for an Article 5 decision.
Albania, regarded by Iran as a “safe haven” for the MeK, is more of an ‘unwitting conspirator’ than a knowing participant in this ongoing cyber conflict.
Declaring Article 5, is a political decision, much like a declaration of war. One is inclined to speculate whether Albania’s fellow NATO members, actively engrossed with the Russian invasion, sought to avoid sparking a ‘second front’ in the Middle East. Albania, opted against Article 5, despite the disruption and destruction of its government services and systems, and chose to cut diplomatic ties with Iran. This move did little to deter Iran from
conducting yet another offensive cyber operations against Albania’s border system.
What has been unfolding is a perfect case of a comprehensive conflict within cyberspace. The most noteworthy observation is the difference in the playing field between sophisticated cyber actors and other countries.
Those countries that have been on the receiving end of cyber action or cyber-enabled espionage, have gone on to develop both their offensive and defensive capabilities. Often taking a traditional military posture that favours strengthening offensive capabilities over defensive capabilities, Iran is a
prime example of this.
On the defensive side, the US has been dealing with offensive cyber action and cyber-enabled espionage from Iran, North Korea, China, and Russia for more than 15 years. NATO members such as the United Kingdom (UK), France, Canada, and Germany have grown to deal with similar threats—albeit within a smaller timeframe. To defend their economies and societies, these nations have spent billions in growing a cybersecurity industry and building defenses against offensive cyber operations.
Escalation in cyber conflict
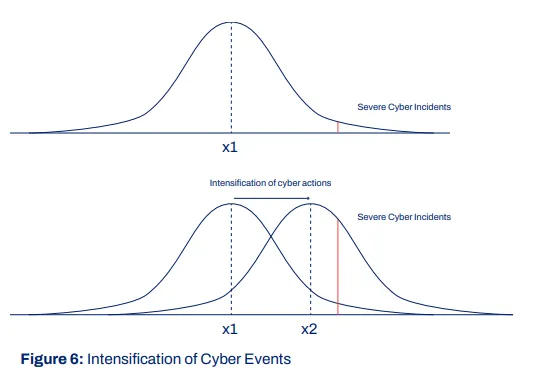
Ironically, this conditioning: building capacity, developing resilience, and strengthening response times, has likely contributed to the
intensification of cyber events that this author and Jason Healey, a Senior Research Scholar at Columbia SIPA, alluded to in December 2021.
 Source: CCDCOE
Source: CCDCOE
Cyber events are now routinely crossing thresholds that would have been viewed as
increasingly risky 20 years ago. The result is that offensive cyber operations are now manageable for countries such as the US but are now catastrophic for smaller countries that are thrust into the cyber conflict space. The potential scale of this effect likely makes smaller countries ideal targets for
sophisticated actors looking to demonstrate their capabilities. Iran appears to have stronger evidence on Israel’s role in the ‘Predatory Sparrow’ campaign (the two countries have been
exchanging attacks for years) but opted to attack Albania’s government for harbouring the MeK—using the disruptive incident to send a message to Iran’s enemies.
This incident is chilling because it shows the spread of sophisticated cyber capabilities, and the growing intent to conduct such operations. Most theories around cyber conflict have kept the US as a key player in such conflicts—‘Predatory Sparrow’ and Iran’s response have shown that this is outdated.
The result is that offensive cyber operations are now manageable for countries such as the US but are now catastrophic for smaller countries that are thrust into the cyber conflict space.
The US does continue to play a tremendous role in how cyberspace is shaped. Over several years, it has taken great strides in developing its cyber policy and responses, both domestically and internationally. The US government was first to
support Albania’s diplomatic decision against Iran, was
quick to sanction Iranian officials over the incident, and US firms and
law enforcement have been involved in the initial incident response and capacity development. However, the US continues to make cyberspace an increasingly
'quintuply dangerous' area of conflict with its
2018 National Cyber Strategy.
The US’ military has an inherently offence-oriented posture with its ‘
Persistent Engagement’ strategy and
‘Hunt Forward’ operations continuing to escalate tensions within cyberspace. These actions are achieved by infiltrating and confronting adversaries within their own networks. These operations can be conducted using
networks belonging to the US’ allies (with and without consent) which could mislead counter-cyber operations.
Whether intentional or not, the US’ policies serve as a benchmark which are subsequently modified for individual countries. For adversaries, these policies are intended to confuse and confound any hope of attribution. This pushes adversaries to look for smaller, less cyber-capable countries that can be made an example of. Such efforts are only making cyberspace more dangerous.
The views expressed above belong to the author(s). ORF research and analyses now available on Telegram! Click here to access our curated content — blogs, longforms and interviews.



 Earlier this month the “
Earlier this month the “


 PREV
PREV


