1. Introduction
Terrorism is defined as the “premeditated use or threat of use of violence by individuals or sub-national groups to obtain political, religious, or ideological objectives through intimidation of a large audience usually beyond that of the immediate victims.”[1] Terrorists mimic randomness to generate fear and panic, and it is a formidable challenge for the targeted country’s government to formulate a strategy that optimally utilises its counterterrorism (CT) resources.[2] Targeted countries are required to invest in their intelligence network as a critical part of their CT efforts.[3] They must also examine the threat posed by various terror groups in terms of their resources and proclivity for conducting attacks, as this present study aims to show.
The majority of deaths from terrorist attacks in different parts of the globe—nearly 58 percent in 2018—are claimed by only four terrorist organisations, namely the Taliban, ISIL, the Khorasan Chapter of the Islamic State, and Boko Haram.[4] Radical doctrines rooted in Wahhabi Islam provide the crucial common denominator for all four groups, even though their strategic objectives may vary. Indeed, historically, many terror attacks have been motivated by religious fundamentalist ideologies of the nature described by Gilling (1992)[5] and Pratt (2006),[6] with religious fundamentalism serving as a political doctrine rather than a spiritual faith (Tibi, 2002).[7]
The purpose of the present paper is to propose a CT framework in terms of three types of CT policies—offensive, defensive, and confidence-building measures (CBMs)— targeted against a terror outfit that is either resource-constrained or resource-abundant. Defensive CT efforts attempt to reduce the optimal number of terror strikes by reducing the (net) operational efficiency with which a terror outfit can attack certain targets. An example is the Anti-Infiltration Obstacle System (AIOS)—a double-row concertina wire fence constructed by the Indian Army along the Line of Control (LoC) to inhibit the infiltration of terrorists from Pakistan-occupied Kashmir (PoK).[8]
For their part, financial and other sanctions or even pre-emptive strikes aimed at destroying the assets of terror outfits constitute offensive CT. For example, a major offensive called ‘Operation All Out’ targeting the top leadership and operational capabilities of NDFB(S) was executed by Indian security forces in Assam, Nagaland and Bhutan in December 2014, in the aftermath of attacks carried out by the outfit which killed over 80 people.[9] Such measures are usually strategic in scope, as opposed to the tactical nature of most defensive measures.
Lastly, incentives may also be given to members or functionaries of a terror outfit in order to induce them to surrender. To this end, so-called confidence-building measures (CBMs) may be undertaken by the government. ‘Operation Sadbhavana’ is an example, launched by the Indian Army in 1998 in rural areas adjoining the LoC.
This paper demonstrates that a government’s CT approach towards an outfit is contingent upon the specific characteristics of that outfit such as its intrinsic propensity for violence, its operational efficiency, and the resources available to it. Therefore, if the specifics of two outfits vary, then a government’s CT approach towards them may also vary.
Arce and Sandler (2005) are of the view that governments tend to prefer deterrence over preemption because of coordination failure in the provision of CT effort. The present analysis contributes to the existing CT literature by establishing and contrasting the limited applicability of offensive CT and CBMs with the widespread utility of defensive CT, without taking recourse to the ‘coordination failure’ argument.
In reality, a government’s CT strategy may involve a combination of different categories of CT measures. For instance, governments often engage in back-channel negotiations with certain terror outfits, even as operations against those groups continue on the ground. Moreover, CT measures (as well as the CT strategy as a whole) chosen by a government to target an outfit may evolve over time, driven by alterations in the outfit’s nature. For example, an outfit that previously was not resource-constrained, may start suffering from paucity of resources over time due to a decline in operational efficiency. Such a change necessitates a corresponding evolution of CT strategy to be employed against the outfit.
An important feature of the present analysis is to characterise equilibria under two different scenarios: one where a concerned terror outfit is resource-abundant, i.e., it has sufficient resources to achieve its desired level of terror activity; and another where the terror outfit is resource-constrained and therefore cannot achieve its desired activity level. This is the case of ‘corner solution’. Results and policies, to a large extent, are hinged on whether the equilibrium is an interior equilibrium or a corner solution. This paper demonstrates that while offensive CT is effective only against resource-constrained outfits, CBMs work only against those that are resource-abundant.
Sandler and Siqueira (2006) theorised that nations confronted by a common terrorist threat can rarely achieve a proper policy mix between deterrence and pre-emption through leadership.[10] The present analysis sharply differs from this thesis. First, this paper does not focus on coordination and externality-related issues between targeted countries when confronted by a common terrorist threat, and therefore it limits its structure to include only one targeted country. Second, in this analysis, all payoffs are derived endogenously from the respective utility functions of each group.
The next section presents the basic model involving terror outfits and the targeted country’s government. Section 3 addresses the problem facing the targeted country, and discusses the ramifications of the results derived in Section 2 on its CT policy. Section 4 discusses the measurement of various parameters pertaining to terror outfits as characterised in Section 2 and provides a ranking of some of the groups mentioned in Section 5, which provides case studies describing the real-world applications of some CT strategies and their consequences. The closing section summarises the key points of the analysis and provides potential directions for future research.
2. Model

3. Implications for Counterterrorism Policy

3.1. Resource-abundance

3.2. Resource-constraint

3.3. Strategy
The following proposition summarises the strategic implications of the above discussion on ad-hoc CT:
Proposition 8: CT strategy in the vicinity of the initial equilibrium should prioritise:
- CBMs, if and only if the targeted terror outfit is resource-rich and sufficiently inefficient (or insufficiently violent);
- Offensive measures, if and only if the targeted terror outfit is sufficiently resource-constrained (or sufficiently inefficient); and
- Defensive measures for all other outfits.
The above proposition is logical. First, a resource-rich outfit has a stronger (or weaker) incentive to respond to CBMs if it is unable (or able) to carry out attacks with sufficient impunity, say due to high-value targets being sufficiently secure (or insecure); or if it is not too violent intrinsically, say because its objectives are political rather than ideological. Thus, follows the first statement. Second, an ad-hoc CT response should be predominantly offensive if and only if governmental efforts to neutralise/squeeze the outfit’s assets have an immediate impact on the ability of the outfit to conduct attacks, without threatening to draw the government into a long-drawn military campaign such as the strategic quagmire in Afghanistan which the United States found itself in against the well-funded Taliban insurgency. This rationalises the second statement. All other outfits are sufficiently efficient and are not highly resource-constrained. CBMs are therefore not very effective and offensive measures threaten to snowball into a long-drawn and expensive military campaign, or are simply ineffective given that the outfit has sufficient resources at its disposal. The government therefore tends to focus primarily on hardening potential targets. This justifies the third statement.
4. Estimation of Parameters
Parameters used to describe a terror outfit, such as intrinsic propensity for violence, operational inefficiency, and resource endowments cannot be directly observed and must therefore be estimated using proxy variables for purposes of analysis. One way of estimating an outfit’s proclivity for violence, for instance, is by using as a proxy variable the number of suicide attacks as a percentage of total attacks conducted by the group during the past year. Similarly, the operational efficiency () of an outfit can be analysed using the lethality of the group’s terror attacks, i.e., the number of fatalities per attack conducted by the group during the last year. Once this is done, the resource-endowment of a resource-constrained outfit can be calculated by substituting the value and the total number of attacks in Equation (7), although this method is inapplicable for resource-abundant groups.
Table 1 provides the values of these proxies for and for the outfits mentioned in the case studies provided in Section 5, for the year 2020.
Table 1: Proxy Values for Parameters of Select Terror Outfits, 2020
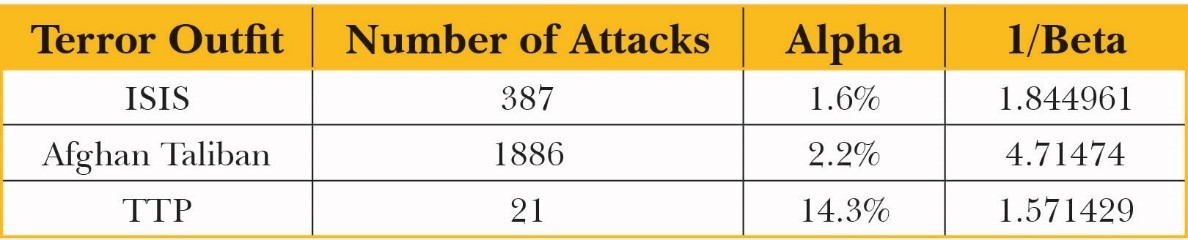
Source: Global Terrorism Database.[14]
Two inferences can be made using the simple method of estimation applied above. First, a terror outfit that is conducting a greater number of attacks need not be intrinsically more violent than an outfit conducting a fewer number of attacks. For instance, TTP seems to be inherently far more violent than the Afghan Taliban and the ISIS despite conducting fewer attacks than those groups. This can be inferred because suicide attacks constituted only 1.6 percent and 2.2 percent of ISIS and Afghan Taliban attacks in 2020, respectively, while they constituted over 14 percent of attacks by TTP.
Second, the TTP is the least efficient outfit among the three in terms of lethality of terror strikes, despite conducting the highest percentage of suicide attacks. Specifically, the group’s attacks resulted in only one-third the casualties per attack that the Afghan Taliban recorded in 2020, and were even less lethal than terror strikes conducted by ISIS the same year. This illustrates that the most violent outfit need not be the most efficient, and might even be the least efficient as shown in Table 1. On the other hand, the outfit which is most efficient, for instance, the Afghan Taliban in Table 1, need not be inherently the most violent.
5. Case Studies
This section discusses real-world instances of the application of different CT strategies and outlines their consequences. The aim is to evaluate their efficacy, and place these in context of the propositions derived in the present study.
5.1. Resource Crunch: Islamic State of Iraq and Syria (ISIS)
In the present study, the specification of a terror outfit’s utility function implies that when faced with dwindling resources, resource-abundant terror groups attempt to reduce only consumption while maintaining their levels of terror activity. If the resource decline persists beyond the juncture where the outfit is having to survive at subsistence levels of consumption, i.e., the point at which the outfit becomes resource-constrained, then the group is forced to reduce terror attacks. Bearing this in mind, this case study looks at how the ISIS (also called Islamic State of Iraq and the Levant or ISIL) dealt with the resource crunch it began to face beginning in late 2015.
Successive events, including the decline in crude oil prices and heightened US-led aerial assaults targeting oil infrastructure and ISIS fighters, had compressed the outfit’s revenues and forced it to depend on the ever-higher taxation of the approximately 8 million people residing in territory occupied under its so-called caliphate by late 2015. Along with the constant exodus of professionals and prohibitions on working women, these factors caused a rise in income inequality between ISIS fighters and common civilians, leading to growing public resentment.
Despite these adversities, ISIS continued to offer relatively generous wages to its rank-and-file over the succeeding few months, until its declining revenues presented the group with the stark choice of either reducing its wage payments or curtailing its high levels of violence.[15] The outfit chose the former, in accordance with the present study’s characterisation of resource-abundant outfits, and discussion in Footnote 3.
Faced with depleting coffers, ISIS implemented salary cuts throughout its so-called caliphate in early 2016, instructing Raqqa inhabitants to settle public utility bills in American dollars sourced from the black market. The group, which used to boast about positioning a new gold-backed dinar as a challenge to the US’s “dollar imperialism”, was struggling to meet costs.
The outfit even put at stake the loyalty of many of its fighters, which had been generated during financially better times in significant measure by using attractive salaries and alluring honeymoon and infant bonuses. The group had also eliminated the supply of goods like costless energy drinks and energy bars. An Islamic State directive sourced by research scholar Aymenn Jawad al-Tamimi of the Middle East Forum stated that “on account of the exceptional circumstances the Islamic State is facing, it has been decided to reduce the salaries that are paid to all mujahedeen by half, and it is not allowed for anyone to be exempted from this decision, whatever his position”.
As far as attacks were concerned, the numbers showed resilience despite the revenue squeeze. Indeed, the attacks rose significantly from over 1,200 in 2015 to a peak of almost 1,500 in 2016, before declining below 1,400 in 2017. It was only thereafter that the number of terror strikes displayed a steep downward trend in accordance with this paper’s Proposition 1, and settled below 400 in 2020—this corresponds to the period during which the outfit seems to have become resource-constrained (see Figure 1). This rapid decline in the outfit’s capacity to conduct terror activities was therefore opposed to al-Tamimi’s prediction of “a scenario of gradual decay and decline.”[16]
Figure 1: Total Number of Terror Strikes by ISIS (2012-2020)
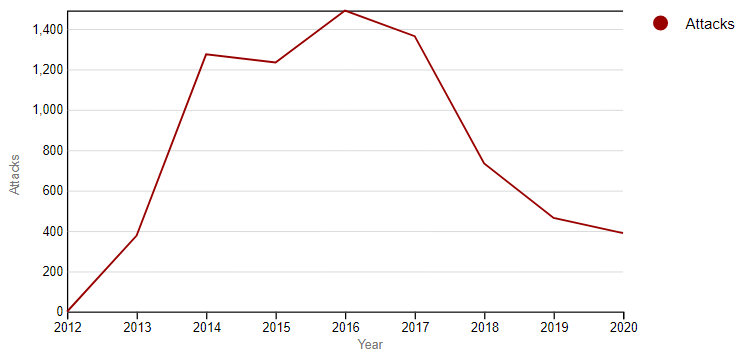
Source: Global Terrorism Database.[17]
5.2. Offensive CT: Afghan Taliban
The US-led Global War on Terror (GWOT) in Afghanistan, launched after the acts of terror conducted by al-Qaeda in September 2001, began with bold declarations of ending terrorism. Even the West’s principal rivals like the Russian Federation and the People’s Republic of China backed the campaign against radicalism. Dozens of thousands of military personnel, the most modern military hardware that existed at the time, and billions of dollars of funding made their way to Afghanistan to support the largest offensive CT campaign the world had ever witnessed until then.
As noted by former UNHCR representative to Rwanda, Saber Azam, 3,600 foreign troops, including 2,500 Americans lost their lives and another 34,000 were injured, and thousands suffered from post-traumatic stress disorder (PTSD) in the following 20 years.[18] Further, approximately 70,000 Afghan troops, 47,000 civilians, and 53,000 Taliban fighters died. Yet, in August 2021, the US and its allies deserted Afghanistan hurriedly, signing the country off to those they had promised to “smoke out”. To understand the primary reason behind the debacle, it is necessary to comprehend the salience of Afghanistan’s narcotics trade in fueling the Taliban.
Just as at the beginning of the GWOT, the Taliban are participating in all aspects of Afghanistan’s opiate economy from poppy sowing, opium extrication, bootlegging, to imposing export levies on smugglers. The Taliban have relied on the narcotics trade as one of their principal income streams, with economies of scale incentivising higher production volumes.
The failure of the GWOT, therefore, can be attributed largely to its inability to effectively squeeze Afghanistan’s illegal narcotics trade.[d] In the words of a US official with understanding of the matter, “We’ve (the U.S. and its allies) stood by on the sidelines and, unfortunately, allowed the Taliban to become probably the largest funded non-designated terrorist organization on the globe”.[19] Thus, the overwhelming evidence has throughout been in favour of the Taliban being resource-abundant for the entire duration of the GWOT, despite US-led efforts targeted at changing the same.
In light of this paper’s Proposition 8 and its discussion, it is therefore no wonder that the resource-rich Taliban’s ability to conduct attacks was not curbed in any noticeable measure by the US-led offensive CT campaign. Indeed, widespread resentment against the presence of foreign troops on Afghan soil seemed to have fueled the spectacular increase in attacks conducted by the Taliban through an increase in the outfit’s intrinsic propensity for violence (see Figure 2).
Figure 2: Number of Terror Strikes by the Afghan Taliban (2000-2020)
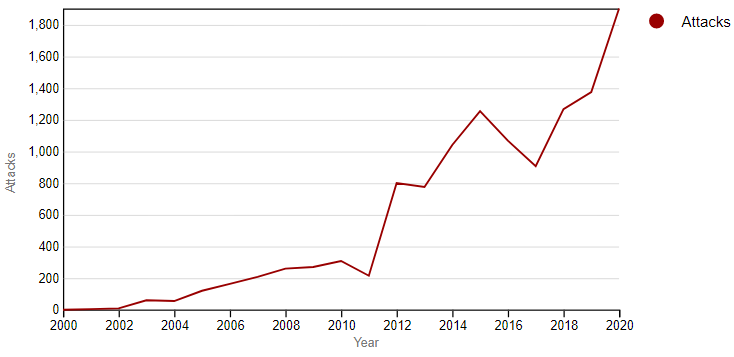
Source: Global Terrorism Database.[20]
An approach based on securing critical infrastructure and Afghan State institutions while meaningfully engaging with the Taliban for a political resolution involving other ethnicities, would have had better odds of reducing violence over time. This strategy would have lowered the group’s inherent propensity for violence while also increasing the costs of terrorist operations, in accordance with this paper’s Proposition 1.
5.3. Offensive CT Vs. CBMs: Tehreek-e-Taliban Pakistan (TTP)
After several years of bloody fighting against the TTP—which gained global notoriety after its December 2014 attack on Army Public School in Peshawar that killed 149 people including 132 students—the Pakistan government decided in 2021 to embark on the route of confidence-building with the outfit. The attack had occurred a few months after Pakistan formally launched an offensive CT campaign, called Zarb-e-Azb, involving air strikes and limited military action in addition to regular cordon-and-search operations.
Despite the initial difficulty and violent reprisals against the State machinery, Zarb-e-Azb was a success, liberating almost the entirety of North Waziristan from the terrorists’ control and severely degrading their resources. Consequently, the number of terror strikes conducted by the resource-constrained outfit witnessed a steep and consistent decline since 2014 in accordance with Proposition 1(b), as illustrated in Figure 3. Instead of continuing with the tried and tested formula of offensive CT against the severely weakened outfit, however, the Pakistani establishment decided to negotiate a ceasefire with TTP largely because of the (Afghan) Taliban’s victory in Afghanistan.
Figure 3: Total Number of Terror Strikes by TTP (2011-2020)
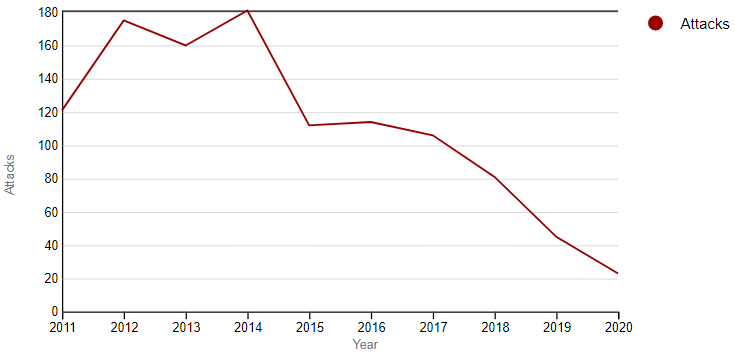
Source: Global Terrorism Database.[21]
In effect since 9 November 2021, the ceasefire has now held for over a year, and yet Pakistan remains on tenterhooks because of an increased threat of terror strikes by TTP. Federal government sources in Pakistan have claimed knowledge of a senior leadership rendezvous of TTP in Afghanistan’s Paktika to deliberate on the impasse in peace talks. Also on the agenda was the group’s response to the killing of its commanders Omar Khalid Khorasani and Aftab Parkay. Such is the nature of the deadlock in negotiations between TTP and the government, that Pakistan’s Ministry of Interior found it important to acknowledge the same in September 2022, and warn of the consequent discomfort within the TTP’s ranks.[22]
The stalemate might seem surprising given that the indefinite ceasefire was announced by TTP as a CBM, after internal consultations. Moreover, the Pakistani administration had responded with its own CBM involving the release of almost 102 TTP prisoners.[23] A closer inspection, however, suggests that the ceasefire was an attempt by TTP to gain some much-needed respite after years of reversals at the hands of Pakistani security forces.
The ceasefire also provided the outfit with an opportunity to regroup and reorganise itself in Pakistan. The recent uptick in terror strikes and show of force through demonstration of arms in Swat and former Federally Administered Tribal Areas (FATA) regions point to the failure of CBMs, in accordance with Proposition 1 of this analysis.
As Pakistani journalist Rashed Rahman has noted, negotiated ceasefires have historically proved nothing more than “tactical measures that were abandoned as soon as the religious extremists felt they could return to the offensive.”[24] The pattern replicated itself since 2004— “such edifying episodes as the terrorists playing football with decapitated soldiers’ heads.” Based on the findings of the present paper, therefore, the Pakistani establishment should take the initiative against the TTP by turning to a combination of offensive and defensive CT measures, rather than waiting for the outfit to dictate terms and escalate at a time of its choosing.
5.4. Defensive CT: AIOS
The AIOS constructed by the Indian Army between 2003 and 2005, along the LoC, resulted in a steep and sustained decline in successful infiltrations by terrorists from PoK. As senior journalist Shabir Ibn Yusuf noted in September 2022, infiltration bids have decreased every year in recent times from 419 in 2017, to 328 (2018), 216 (2019), 99 (2020), and 77 (2021).[25] Consequently, the incidents of killing in the erstwhile Indian State of Jammu and Kashmir declined from 1,642 in 2002 to 1,427 in 2003, further to 1,061 in 2004, 1,004 in 2005, 694 in 2006, 427 in 2007, and 261 in 2008 (see Figure 4).[26]
Figure 4: Fatalities in Jammu and Kashmir (1988-2000)
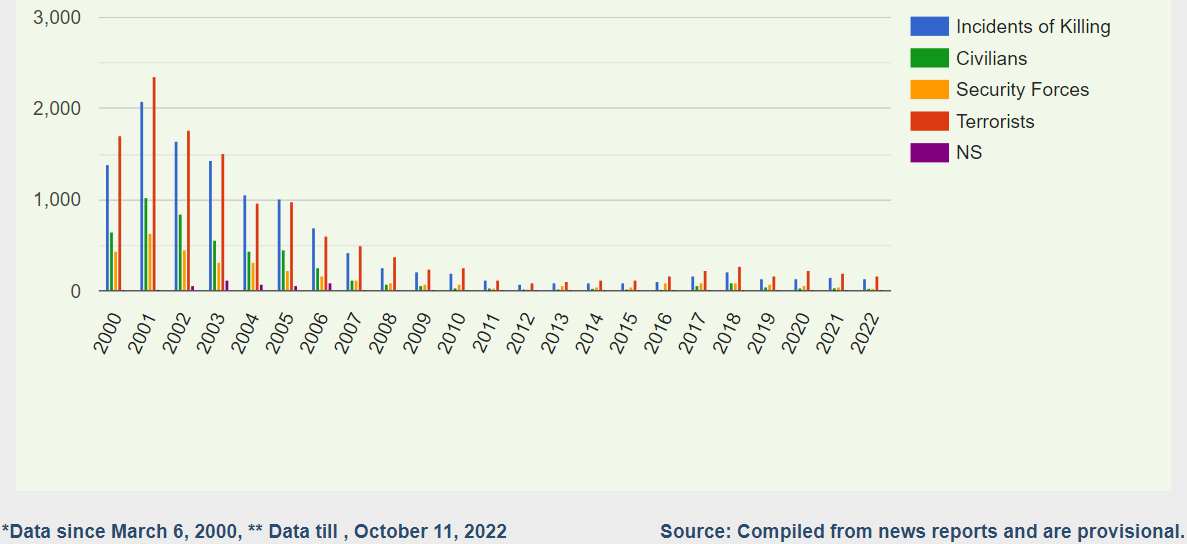
Source: South Asia Terrorism Portal.
The AIOS includes border fencing, electrical live wires, sensors, sirens, foot patrols, floodlights as well as other surveillance devices like hand-held thermal imagers. The success of this defensive CT endeavor is especially spectacular given that the AIOS is constructed along one of the most hostile terrains globally, that experiences extensive snowfall and avalanches during winters as well as landslides and floods during monsoons—this is in accordance with Proposition 1(a) of this paper.
In recent years, the Indian Army has implemented an effective counter-infiltration strategy and increased the induction of different platforms to enhance the surveillance architecture, apart from maintaining stricter vigil along the LoC. In 2021, the Ministry of Defence stated that “(the Indian) Army has adopted a robust counter-infiltration strategy which has an appropriate mix of technology and human resource put together to check infiltration effectively. Innovative troops deployment, proactive use of surveillance and monitoring devices, and the Anti Infiltration Obstacle System (AIOS) has enhanced the ability to detect and intercept militants attempting to infiltrate/exfiltrate.”[27] The sustained decline in infiltration attempts mentioned earlier, comes as no surprise therefore, and is expected to sustain in the future.
6. Conclusion
The present work explored the impact of various CT measures targeted against self-funded terror outfits. A key inference borne out of this effort is that defensive measures are a ubiquitous component of CT. This is because such measures reduce the efficiency with which terror outfits can use their scarce resources, thereby making them a reliable choice in the context of any CT effort. In contrast to the ubiquity of defensive measures, this paper finds CBMs and offensive CT measures to have limited applicability, as these are demonstrated to only be of use against a resource-rich and a resource-constrained terror outfit, respectively.
CBMs can inhibit the activity of resource-rich terrorists by reducing their inherent propensity for violence, while offensive measures can curtail the activity of a resource-constrained terror group by causing the degradation of its resources. This contributes to the existing literature which only demonstrates the general over-investment in defensive measures and under-investment in offensive measures,[28] the inability of countries to arrive at the optimal CT mix between offence and defence when faced with a common terrorist threat,[29] and the inability of the State to win a war-on-terror using preemption alone as long as the marginal cost of preemptive measures is increasing.[30]
The importance of this present analysis lies in its novel rationalisation of the omnipresence of defensive CT on the basis of the above-mentioned efficiency-of-resource-use hypothesis. This paper specifically demonstrates that when dealing with a resource-abundant terrorist group, the strategy should be biased toward defensive CT and away from CBMs with higher level or intensity of terror activity, and vice versa. In the context of resource-constrained outfits, on the other hand, the strategy should be biased away from offensive CT and toward defensive CT if the terror outfit has a higher resource base or is more operationally efficient. These insights are applicable to CT efforts worldwide, as the case studies provided in Section 4 amply demonstrate.
The paper also suggests ways by which the parameters pertaining to a terror outfit can be quantified using proxy variable estimation, and provides an example in Section 4 involving terror outfits mentioned in the case studies provided in Section 5. It readily followed that a terror outfit conducting a greater number of attacks need not be intrinsically more violent than an outfit conducting a fewer number of attacks, and the most violent outfit need not be the most efficient, and might even be the least efficient. On the other hand, the outfit which is most efficient need not be inherently the most violent.
A logical extension of this work would be to scrutinise real-world applications of various CT strategies and their effectiveness by quantifying the resulting variations in parameters using proxy variables for the same, as discussed in Section 4. This would enable an estimation of the sensitivity of terror activity to variations in each parameter as estimated by its respective proxy variable.
Appendix
The views expressed above belong to the author(s). ORF research and analyses now available on Telegram! Click here to access our curated content — blogs, longforms and interviews.

 PDF Download
PDF Download












 PREV
PREV


