-
CENTRES
Progammes & Centres
Location

Utsav Mittal, “A New Framework for a Secure Digital India,” ORF Issue Brief No. 422, November 2020, Observer Research Foundation.
Introduction
Across the globe, governments are putting national security considerations at the centerstage of their regulatory interventions. These regulations cover domains that in recent years have included non-traditional security concerns. In the area of investments, for example, many countries have modified their rules, two and a half decades since the establishment of the global trade order under the aegis of the World Trade Organization.[1] Globally, foreign investments worth more than US$ 150 billion have either been blocked or withdrawn for national security reasons in the period from 2016 to September 2019.[2] For instance, the president of the United States (US) prohibited the proposed takeover of chipmaker Qualcomm by Singapore-based Broadcom for national security reasons.[3]
More recently, such national-security compulsions have guided rule-making in the area of digitalisation. The Indian government, for example, has banned more than 150 China-origin applications due to security concerns.[4] In the US, the president issued in August this year, two executive orders to restrict transactions by US users and entities with ByteDance and Tencent, both China-owned corporations, which own the popular social media platforms, TikTok[5] and WeChat.[6] Other notable instances of such actions include Russia’s barring of the use of LinkedIn in 2016[7] and the US’ ban on Russian security company, Kaspersky.[8]
Rules governing the behaviour of digital players are evolving as nations experiment with different approaches and consider diverse policy priorities and objectives. Governments are increasingly concerned about protecting personal information, and arresting the incidence of cybertheft that has affected consumers and businesses. On 16 June 2020, India’s Computer Emergency Response Team (CERT-In) issued an advisory that large-scale phishing attacks may be launched against Indian businesses.[9]
The imperative is to find a balance between trade priorities and national security. Indeed, digitalisation has made economies vulnerable to security threats. This is because of the nature of the internet being a bidirectional medium that offers an enhanced level of access to information about individuals, thereby potentially compromising their privacy and security. Social-media platforms, for example, make users susceptible to manipulation. There have been cases in different parts of the world of threat actors using social media to influence electoral outcomes and threaten social stability.[10]
According to the Organisation for Economic Cooperation and Development (OECD)’s Digital Trade Service Restrictiveness Index, only four countries out of 46 surveyed by the OECD have lowered their trade barriers during the period 2014 to 2019.[11] The majority either heightened their digital services trade restrictiveness or maintained the same level. In India, restrictiveness index increased from 0.21684 to 0.34339 during the same period.
Figure 1. Digital Services Trade Restrictiveness Index (2019)
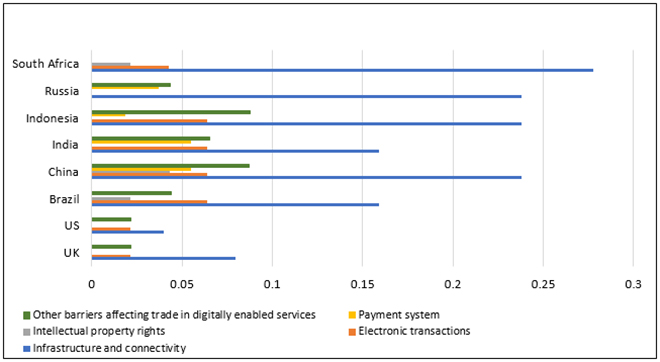
This brief outlines a plausible strategy that will help India address its national security concerns whilst ensuring an open trade environment.
National Security Considerations
Sovereign nations are equipped with wide powers to deal with what they themselves define as challenges to their national security. This allows governments to respond to different threats that may evolve or emerge over time. A strategy aimed at addressing these concerns must be underpinned by a concrete understanding of what comprises “national security”, to begin with.
Security risks can be categorised into two broad classes: internal (homeland) security, and external security. These threats are further classified as externally-aided internal, and internally-aided external risks. Internal homeland security deals with issues related to public order within the country. In India, the Ministry of Home Affairs lists the following key issues in the country’s internal security: a) terrorism in the hinterlands; b) Left-Wing Extremism in specific areas; c) the security situation in Jammu and Kashmir; and c) insurgency in the northeastern states. External security, as the name suggests, is concerned about the security risks emanating from outside India’s borders.
In an increasingly globalised and connected world, the line between internal and external threats can get increasingly blurred. The emergence of data-driven businesses has caused fundamental shifts in the Indian and global economy alike, leading to new modes of communication and information-sharing, business models, and sources of job growth. India is also fast approaching around 700 million broadband users and will see millions more over the next few years.[13]
Cyber security finds its roots in traditional military principles: many of its basic covenants have been adopted from traditional military security principles such as “need-to-know” and “least-privilege”.[a] To begin with, the internet as the world knows it today, has evolved from military technology— i.e., the Advanced Research Projects Agency Network (ARPANET).[14] Over the years, it has had a transformational impact across the globe.
In India, this has three interrelated elements: the unprecedented adoption of smartphone use in the country; the presence of a young and technology-savvy population, and affordable access to internet services and devices. Furthermore, the push for digitalisation by the government, through flagship initiatives under the overarching ‘Digital India’ banner, is also a key driver of the ongoing digital transformation.[15]
Indeed, the government’s digitalisation efforts have been buoyed by the restrictions on movement that were put in place to respond to the COVID-19 pandemic. Consumers are using digital applications to buy consumer durables and necessities, for telemedicine, and for connecting with their friends and family. According to the Reserve Bank of India (RBI), India is recording around 100 million digital transactions every day, with a volume of INR 5 trillion ($67 billion).[16] This represents approximately a five-fold increase from the 2016 levels. The RBI expects digital transactions to continue on a growth trajectory; estimates suggest an increase to 1.5 billion transactions a day worth INR 15 trillion by 2025.[17]These figures show that even as the Indian economy has suffered a slowdown because of the pandemic, the country’s digital retail market has earned.
At the same time, cyberattacks have surged. India saw a 37-percent increase in cyberattacks in the first quarter (Q1) of 2020, as compared to the fourth quarter (Q4) of the previous year, according to the Kaspersky Security Network.[18] As India’s workforce shift to remote infrastructure, instances of identity theft, and malicious payload delivery has witnessed a spike.[19] Breaches by information-stealing malwares like AZORult have been observed in India—they are used to steal users’ browsing history, cookies, IDs and passwords, cryptocurrency, and are also able to download additional malware onto devices.[20]
The threats to national security can be far more insidious. In the United States (US), for instance, the data consulting firm Cambridge Analytica was exposed to having used Facebook to access the personal data of almost 50 million profiles and influence the outcome of the US elections. The data were catalogued into psychological profiles, allowing Analytica to build an algorithm that skewed news results in those users’ Facebook news feeds.[21] Scholars have argued that such incidents are continuously testing the conventional understanding of the nature of risks to national security.[22]
Following the revelation in March 2018, India’s Expert Committee on Data Protection, headed by Justice (retd.) B.N. Srikrishna, noted:
“the incident (Facebook-Cambridge Analytica), unfortunately is neither singular, nor exceptional. Data gathering practices are usually opaque, mired in complex privacy forms that are unintelligible, thus leading to practices that users have little control over.”[23]
India’s Approach: An Evaluation
Governments regard strategic industries and critical infrastructure as key to countering internal and external threats to national security. “Strategic industries” include those that are crucial for the economic development of a country; “critical infrastructure” are sectors that are vital not only for the economy, but on other pillars of society as well (e.g. power, transportation, and finance).
India’s Information Technology (IT) Act defines Critical Information Infrastructure (CII) as computer resources whose incapacitation or destruction will have debilitating effects on India’s security, economy, public health, or safety.[24] The National Cyber Security Policy (NCSP) 2013 delineates CII protection as a national priority that requires the sharing of responsibility between the public and private sector. The policy outlines the importance of establishing a National Critical Information Infrastructure Protection Centre (NCIIPC).
The Indian government has thus established a nodal NCIIPC under the National Technical Research Organisation (NTRO), the intelligence agency under the Prime Minister’s Office.[25] The NCIIPC’s key functions include: identifying all elements of CII for government approval; issuing threat-related advisories; and offering requisite leadership and coordination to effectively respond to threats against identified CIIs. It is also assigned the responsibility to coordinate and share strategic information with the CERT-In.[26]
At present, CIIs under each critical sector are identified based on parameters such as “functionality; criticality; scale; degree of complementarities; political, economic, social and strategic values; degree of dependence; and sensitivity.[27]There are six critical sectors, according to the government’s definitions: banking, financial services, and insurance; transport; telecommunications; power and energy; government; and strategic and public enterprises. Operational technology (OT)—which helps in monitoring, managing, and controlling physical devices and related functions—is a vital cog within the CII sectors.[28] These systems are collectively known as cyber physical systems. Cyberattacks on cyberphysical systems can therefore risk disruption of services in the critical sectors such as hydropower plants and dams, satellites, power plants, and electricity grids. Reliance on OT due to increased digitalisation, has in turn heightened the vulnerabilities of CIIs.
Categorising certain sectors as “critical” allows the government to focus its enforcement activities on the most vulnerable and high-impact sectors. This is especially required for a country like India where capacity constraints hamper the government’s management of each and every threat that exists. Indeed, such graded and risk-based approach is increasingly being adopted by many other countries across the globe.
To begin with, “risk” is understood as the combination of the likelihood of an adverse event (hazard, harm) occurring, and of the potential magnitude of the damage caused (itself combining the number of people affected, and severity of the damage for each).[29] In contrast to a one-size-fits-all approach, a risk-based approach is tailored, providing benefits to consumers and businesses alike.
The US’ National Institute of Standards and Technology (NIST) maintains that risk-based approaches help ensure network security, as more effective investment decisions are made with better measurements of risks, costs, and benefits of cybersecurity strategies.[30] Similarly, Germany has designed rules specific to social-media intermediaries. Germany’s Netzwerkdurchsetzungsgesetz (NetzDG), also referred to as the Network Enforcement Act, applies to social network platforms with more than two million users.[b],[31] These threshold limits are an acknowledgment of the network effects[c] that play out on large social-media platforms.
These graded approaches are not new to India. The Personal Data Protection Bill, 2019 proposes to designate certain data fiduciaries i.e. entities collecting and processing personal data as “significant data fiduciaries”. Section 26 of the Bill provides that the Indian government designate a social media company whose actions have, or are likely to have a significant impact on electoral democracy, the security of the State, public order, or the sovereignty and integrity of India as a significant data fiduciary, in consultation with the proposed Data Protection Authority.[32] The rationale behind this is to distinguish and place additional obligations on entities that are capable of causing significantly greater harm to Indian users as a consequence of their data processing activities. Similarly, RBI has differential Master Directions for IT and cybersecurity, for NBFCs having asset size above and below INR five billion.[33]
Tackling the Threats
After the identification of relevant entities from a security standpoint, India can follow a three-pronged approach to developing the country’s cyber-resilience.
Standardisation is a crucial component in developing cyber-resilience. Often seen as an obligation that drains resources, standardising information-security protocols helps by improving the effectiveness and efficiency of cyber-defense processes; facilitating interoperability and systems integration; simplifying complex cyber environments; and deploying new technologies and business solutions.[34]
India’s Information Technology Act, 2000, lays down regulations for data security. Specifically, Section 43A of the Act[35] and the Rules on sensitive personal data (SPD Rules)[36] provide for the maintenance of reasonable security practices. Rule 8 defines “reasonable security practices” as the implementation of security practices and standards, a comprehensively documented information security program, and information security policies that contain managerial, technical, operational, and physical security control measures commensurate with the information assets being protected and the nature of the business. The ISO/IEC 27001 international standard is a recognised standard under the SPD Rules. [d]However, there is little evidence of strict enforcement.
India can consider adopting ISO 27701, which is considered as a privacy extension of the 27001 standard.[37] The ISO 27701 standard helps an organisation in establishing a framework for the protection of privacy, provides guidance on how institutions should handle sensitive personal data, and helps in demonstrating compliance with different privacy regulations across the world. It also specifies a Privacy Information Management System (PIMS) and provides a framework for managing Personally Identifiable Information (PII).
The use of the Common Criteria Certification Scheme, which has been adopted by jurisdictions such as the US, Singapore, and the European Union, also offers a useful alternative. For reference, the Common Criteria for Technology Security Evaluation is an international standard (ISO/IEC 15408), that provides an infrastructure within which participating organisations can specify functional and assurance requirements, businesses can develop and claim specific product qualities, and testing facilities can examine products to determine whether they meet those claims. Evaluation Assurance Level (EAL) is assigned to a computer system after the evaluation, which indicates the level at which a system was tested. Domestic regulators such as the Securities and Exchange Board of India (SEBI) have also embraced the Common Criteria Scheme.[38]
A critical advantage of mandating Common Criteria Certification to a specific entity is the relative ease in rolling out such obligations. India is already a member of the Common Criteria Mutual Recognition Arrangement (CCMRA). This arrangement enables the recognition of evaluation done by one member country in another. More than 30 countries have signed the arrangement so far, including the US, Singapore, Japan, Canada, and Australia.[39]
In India, the Standardisation Testing and Quality Certification (STQC) Directorate, which is attached to the Ministry of Electronics and Information Technology (MeitY) acts as the Certification Body. The Directorate has established testing centers in West Bengal, Maharashtra, Karnataka, and Delhi.
A comprehensive data protection framework is vital to lay down the do’s and don’ts for 21st-century businesses. India’s effort to draft its data protection legislation began in 2017 with the establishment of the Committee of Experts under the chairmanship of Justice (retd.) B.N. Srikrishnan. Since 2017, a white paper has been released,[40] as well as a report of the Committee of Experts[41]and two bills (in 2018[42] and 2019[43]). The Joint Parliamentary Committee is in the process of examining the latest draft of the Personal Data Protection Bill.[44]The Parliamentary Committee was supposed to submit its report by the last week of March 2020. However, due to the ongoing pandemic, the deadline has been extended to the second week of the Parliament’s winter session.[45]
The 2019 version of the Bill places restrictions on cross-border transfer of sensitive and critical data. Critical personal data may only be processed in India, as per the Bill. The Bill also calls for mandating data security audit obligations on significant data fiduciaries and providing legal backing to the anonymisation of data sets. The Bill establishes a Data Protection Authority to supervise relationships between data fiduciaries and data principal, i.e. individuals to whom the data relates. These measures are critical in responding to cyber-threats and from an enforcement standpoint as well.
Building a cyber-resilient society is a shared responsibility of the private sector and government. Apart from developing organisational resilience to cyber threats, it is critical to sensitise users about digital risks. The Indian government will have to encourage private parties that meet the threshold detailed earlier in this brief, to spend a specific percentage of their revenue towards cybersecurity awareness initiatives.
This can be done along the lines of the corporate social responsibility framework (CSR). Section 135 of the Indian Companies Act, 2013[46] mandates every company having a net worth of INR 5 billion or more, or turnover of INR 10 billion or more or a net profit of INR 50 million or more during any financial year to spend at least two percent of its average net profits during the three immediately preceding financial years for CSR. In this regard, Schedule VII of the Act[47]provides a list of activities that can be considered as a CSR activity. A similar framework for digital platforms, above a certain threshold, should be explored.
Recommendations
The Indian government should consider adopting a risk-based and graded approach to counter national security risks posed by digitalisation. This brief recommends a holistic assessment based on the following criteria:
Box 1. Applying the graded approach to banned applications
|
On 2 September 2020, the Ministry of Electronics and Information Technology (MeitY) banned 118 applications for reasons of national security. To apply the graded approach, this brief takes a sample of 10 out of the 118 applications. Rangers of Oblivion, Web Browser – Secure Explorer, Baidu, Apus launcher, Apus Flashlight, Gallery Vault, Government WeChat, Carrom Friends, Hide App – Hide Application, and Smart App Lock. Out of these 10, only 3 applications i.e. Carrom Friends, Hide Application, and Smart App Lock have more than five million users each. For ease of reference, five million users have been used as the threshold for the number of users[1]. Smart App Lock and Hide Application required permission like access to location, camera, fingerprint, and network usage history. Consequently, they gain access to the user’s geo-location and biometric-data. While Carrom Friends only requires minimal and necessary permissions like access to the network and preventing the screen from dimming. Therefore, only two applications (out of 10) would qualify for scrutiny under the graded approach. |
Conclusion
The number of internet users in India is expected to reach one billion by 2025.[48]As consumers shift increasingly to digital alternatives, businesses are also innovating constantly to serve changing needs. A distinguishing feature of the 21st century data-driven businesses is their ability to innovate at a brisk pace. This allows them to consistently tweak their business models to cater to dynamic consumer demands. However, as data-driven businesses occupy centerstage in the global economy, the concomitant cyber-threats raise security concerns for governments across the globe.
India will have to carefully curate a strategy to ensure that the country can exploit the economic potential of the digitalisation of the economy, while developing cyber-resilience. Such a strategy should be underpinned by trust and confidence between businesses, government, and consumers. One method of achieving this is to work towards a standards-based framework. The Common Criteria Certification Scheme along with ISO 27001/27701 can be used to mitigate security risks. In this context, a graded approach to scrutinise digital businesses based on thresholds provided in this brief—or any other threshold determined by the government—can allow the effective allocation of finite government resources. In addition, such an approach can ensure that small businesses and startups are not overburdened with compliance costs. To put it differently, businesses that cross thresholds should be mandated to get their IT systems certified against the applicable standards, while the certification remains voluntary for others.
Besides developing a robust technical infrastructure to minimise cyber-risks, other measures such as the enactment of a data protection law, and encouraging businesses to train and educate the workforce should be pursued. These measures can help in tackling the ever-evolving cyber threats and risks, and lay the foundation for a safe and secure future.
About the Author
Utsav Mittal is a Certified Information Systems Security Professional (CISSP), and a graduate of CERIAS, Purdue University, Indiana. He is CEO and Founder at Xiarch, A Pure Play Cyber Security, Risk and Compliance services provider. He is also the President and founder at (ISC)^2 Delhi chapter. He can be reached at [email protected].
Endnotes
[a] These principles are premised on the idea that every entity or every user of the system should operate using the least set of privileges necessary to complete the job. Primarily, it limits the damage that can result from an accident or error. See Fred B. Schneider, ‘Least Privilege and More’
[b] The country’s population is 83 million.
[c] ‘Network effects’ take place when a platform links multiple sides of a market in ways that are increasingly valuable to those on one side, as the number of participants on the other side increases. Therefore, the influence and impact of social media sites multiply with larger numbers of users.
[d] ISO/IEC 27001 was developed by the International Organization for Standardization and the International Electrotechnical Commission in 2005. The standard provides specification for an information security management system (ISMS) to manage information security vulnerability.
[1] The United Nations Conference on Trade and Development, World Investment Report, 2019, June, 2019, United Nations Publications, New York.
[2] The United Nations Conference on Trade and Development, National Security-Related Screening Mechanisms for Foreign Investment: An Analysis of Recent Policy Developments, November, 2019, New York, UNCTAD.
[3] The White House, “Presidential Order Regarding the Proposed Takeover of Qualcomm Incorporated by Broadcom Limited,” March 12, 2018, Executive Order.
[4] Ministry of Electronics and Information Technology, Government of India, also see Ministry of Electronics and Information Technology, Government of India.
[5] The White House, Addressing the Threat Posed by TikToK, August 06, 2020, Executive Order No. 13942.
[6] The White House, Addressing the Threat Posed by WeChat, August 06, 2020, Executive Order No. 13943.
[7] Ingrid Lunden, “LinkedIn is now officially blocked in Russia”, Techcrunch, November 17, 2016.
[8] Dustin Volz, “Trump signs into law U.S. government ban on Kaspersky Lab software”, Reuters, December 13, 2017.
[9] Indian Computer Emergency Response Team, “COVID related Phishing Campaign by Malicious Actors”, June 19, 2020, Advisory No. CIAD 2020-0040.
[10] Samantha Bradshaw, and Philip. N. Howard, “Challenging Truth and Trust: A Global Inventory of Organized Social Media Manipulation”, Oxford, UK: Project on Computational Propaganda.
[11] The Organisation for Economic Cooperation and Development, Digital Services Trade Restrictiveness Index.
[12] The Organisation for Economic Cooperation and Development, Digital Services Trade Restrictiveness Index
[13] Statista, “Number of internet users in India from 2015 to 2020 with a forecast until 2025”.
[14] John Naughton, “The evolution of the Internet: from military experiment to General Purpose Technology”, Journal of Cyber Policy, Vol. No.1, 5-28 (2016).
[15] Government of India, Digital India.
[16] Anup Roy, “Digital transactions could reach Rs 15 trillion a day by 2025: RBI”, Business Standard, July 22, 2020.
[17] Anup Roy, “Digital transactions could reach Rs 15 trillion a day by 2025: RBI”
[18]“37% increase in cyberattacks in India in Q1 2020: Report”, The Economic Times, May 25, 2020.
[19] PwC, COVID-19 Crisis – The impact of cyber security on Indian Organisations, April, 2020.
[20] Regina Mihindukulasuriya, “How hackers are using coronavirus panic to target India through WhatsApp and email”, The Print, March 12, 2020.
[21] Ünver, H. Akın, “Politics of Digital Surveillance, National Security and Privacy”, Centre for Economics and Foreign Policy Studies, 2018.
[22] Shruti Pandalai, “The ‘Social Media’Challenge to National Security: Impact and Opportunities A Conceptual Overview”, Institute for Defence Studies and Analyses, Monograph No. 55, 2016.
[23] Committee of Experts under the Chairmanship of Justice B.N. Srikrishna, A Free and Fair Digital Economy – Protecting Privacy, Empowering Indians, July 2018.
[24] Information Technology Act (as amended in 2008), s 70(1).
[25] Notification No. 9(16)/2004-EC, January 2014, https://www.meity.gov.in/writereaddata/files/gazette_11-01-2014.pdf
[26] The Information Technology (National Critical Information Infrastructure Protection Centre and manner of performing functions and duties) Rules, 2013, See Rule 4
[27] National Critical Information Infrastructure Protection Centre, ‘Guidelines For The Protection Of National Critical Information Infrastructure’ (National Critical Information Infrastructure Protection Centre 2015)
[28] Access Partnership, Cybersecurity Policy for Operational Technology – A Guide for Governments, October 07, 2020, https://www.accesspartnership.com/cybersecurity-policy-for-operational-technology-a-guide-for-governments/
[29] OECD (2018), OECD Regulatory Enforcement and Inspections Toolkit, OECD Publishing, Paris, https://doi.org/10.1787/9789264303959-en.
[30] National Institute of Standards and Technology (U.S.), Framework for improving critical infrastructure cybersecurity, 2018, https://nvlpubs.nist.gov/nistpubs/CSWP/NIST.CSWP.04162018.pdf
[31] Network Enforcement Act (Netzdurchsetzunggesetz, NetzDG)
https://germanlawarchive.iuscomp.org/?p=1245
[32] The Personal Data Protection Bill, 2019, http://164.100.47.4/BillsTexts/LSBillTexts/Asintroduced/373_2019_LS_Eng.pdf
[33] The Reserve Bank of India, Master Direction – Information Technology Framework for the NBFC Sector, July 08, 2017, https://www.rbi.org.in/Scripts/BS_ViewMasDirections.aspx?id=10999
[34] Sidharth Deb, Towards a cyber-security roadmap for digital payments, April, 2019, Observer Research Foundation, New Delhi,
, https://www.orfonline.org/research/towards-a-cyber-security-roadmap-for-digital-payments-49858/
[35] The Information Technology Act, 2000, https://www.indiacode.nic.in/bitstream/123456789/1999/3/A2000-21.pdf
[36] The Information Technology (Reasonable security practices and procedures and sensitive personal data or information) Rules, 2011, https://www.wipo.int/edocs/lexdocs/laws/en/in/in098en.pdf
[37] The International Organization for Standardization, Security techniques — Extension to ISO/IEC 27001 and ISO/IEC 27002 for privacy information management — Requirements and guidelines, August, 2019, https://www.iso.org/standard/71670.html
[38] The Securities and Exchange Board of India, Cyber Security & Cyber Resilience framework for Stock Brokers / Depository Participants, December 03, 2018,
[39] The Common Criteria, Members of the CCRA.
[40] The Ministry of Electronics and Information Technology, White Paper of the Committee of Experts on the Data Protection Framework for India, December 2017.
[41] Committee of Experts under the Chairmanship of Justice B.N. Srikrishna, A Free and Fair Digital Economy – Protecting Privacy, Empowering Indians, July 2018.
[42] The Personal Data Protection Bill, 2018.
[43] The Personal Data Protection Bill, 2019.
[44] Joint Parliamentary Committee on the Personal Data Protection Bill, 2019.
[45] Aditi Agrawal, Parliamentary committee’s report on Data Protection Bill now due in Winter Session, Medianama, September 24, 2020.
[46] Section 135, the Companies Act, 2013.
[47] Schedule VII, the Companies Act, 2013.
[48] John C., “India estimated to reach 1 billion internet users by 2025”, AtlasVPN, September 23, 2020.
The views expressed above belong to the author(s). ORF research and analyses now available on Telegram! Click here to access our curated content — blogs, longforms and interviews.

Utsav Mittal is a Certified Information Systems Security Professional (CISSP) and a graduate of CERIAS Purdue University Indiana. He is CEO and Founder at Xiarch ...
Read More +