Introduction
Geopolitical rivalries in the cyber domain have intensified in recent years due to continuing tensions between global powers. Certain states have executed cyberattacks against their adversaries targeting national and commercial computer networks, sabotaging critical infrastructure operations, and stealing sensitive data. In some cases, they have used proxy actors such as cybercriminal gangs and hacking syndicates to commit cybercrimes against their adversaries. Recent major cyberattacks include the breach of Indian power grids by Chinese hackers reported in April 2022, the breach of US government agencies by suspected Chinese hackers in March 2022, the disruption of Ukrainian government websites days before the Russian invasion in February 2022, and a ransomware attack against oil terminals in Belgium and Germany in February 2022.[1] This targeting of national, commercial, and critical infrastructure computer networks demonstrates that malicious cyber activities imperil national and economic security.
Indeed, as competition and conflict in cyberspace have thrived, efforts for the creation of common cyber norms are stalled by the polarisation between the western camp (i.e. the United States, its allies, and European countries) and the eastern camp (led by China and Russia). Individual states have had to explore tools to tackle emerging cyber threats. Since 2015, the United States (US) and the European Union (EU) have utilised the tool of cyber-sanctions against their adversaries, primarily targeting Russian, Chinese, and North Korean intelligence operatives and their proxies like the North Korea-backed Lazarus hacking group.
Cyber-sanctions can be defined as autonomous or unilateral economic sanctions and trade restrictions imposed by individual states to deter and punish their adversaries for malicious cyber activities and ensure accountability.[a] [2]
The frequent use of the cyber-sanctions instrument by Western countries[b] raises the question of why they rely heavily on this coercive tool. Other questions relate to whether such sanctions have shaped the bad actors’ ability to engage in malicious cyber activities, and what significant challenges are encountered by states in imposing these sanctions.
This paper seeks to answer these questions by examining the concept of cyber-sanctions and their efficacy in deterring cyber sabotage. The aim is to highlight the evolution of cyber-sanctions and key trends in their implementation. It concludes with an exploration of whether this policy tool is relevant for India and what factors it should consider in using sanctions to tackle cyber maleficence, in particular from China and Pakistan.
The Western Autonomous Cyber-Sanctions Regime: An Overview
States that suffer cyber sabotage have mostly responded by launching retaliatory cyberattacks and hacking into their adversaries’ systems. The spate of retaliatory attacks, for instance, between the US and Russia, the US and North Korea, or Iran and Israel, illustrates this tendency for punitive action.[3],[4] However, as the consequences of cyberattacks worsened in the last few years, national security establishments began debating the need to adopt a more coercive and proactive posture to counter malicious cyber activities. This has become particularly critical as many cyberattacks have caused significant disruptions, short of what is considered the equivalent of an ‘armed attack’ that causes casualties and damage or destruction of property.
In some cases, such acts of sabotage lowered the states’ threshold for military retaliation—at least towards the non-state actors.[5] For instance, in August 2015, the US military targeted an operative of the Daesh terrorist group in an airstrike in Syria, who had exposed the personal data of about 1,300 American military and government employees.[6] In May 2019, the Israeli military bombed the Hamas terrorist group’s technology division based in the Gaza Strip to pre-empt a cyberattack.[7] While these examples are exceptions, states with requisite military capabilities will utilise this option when they see a suitable opportunity to prevent cyberattacks that could cause more harm.
Necessary as they were, however, these military actions did not deter the malicious cyber activities and only highlighted the blunted edge of existing policy instruments. Realising the risk posed by these cyberattacks to their national security and economic prosperity, Western countries looked for other instruments other than military action, to signal that malevolent cyber acts would not go unchecked.
In this context, cyber-sanctions emerged as a preferred tool for these Western governments, as defined in this paper. Since they had already become prolific in using coercive economic sanctions and trade restrictions against their adversaries—the same antagonists from where the cyber threats are emanating—the US and its allies found it convenient to activate cyber-sanctions as an extension of economic sanctions, to retaliate against the chronic cyberattacks and threat actors.
In February 2012, as a counter-terrorism measure, the administration of then US President Barak Obama designated the Iranian Ministry of Intelligence and Security for collaborating with the Hezbollah terrorist group in hacking activities.[8] Yet, it was in January 2015 when sanctions as a tool in response to a specific cyberattack were first used, when the North Korea-sponsored threat actor Lazarus group targeted Sony Pictures Entertainment, allegedly in retaliation for the satirical movie ‘The Interview’ based on the North Korean ruler, Kim Jong-un.[9] The hackers stole sensitive data in that breach, including confidential emails, business plans, and employee details. That hacking reportedly cost Sony some US$ 100 million in the short term, and far more subsequently in cybersecurity measures and employee lawsuits.[10]
Responding to the Sony hack, the US Treasury Department sanctioned three North Korean entities and 10 individuals, including a government intelligence agency and a North Korean arms dealer.[11] As a follow-up, in April 2015, the US issued Executive Order 13694 creating a new sanctions regime aimed at threat actors engaged in malicious cyber activities.[12] These included targeting critical infrastructure, Distributed Denial of Service-type disruptive attacks, and activities causing a misappropriation of funds or economic resources, loss of trade secrets, and financial and personal information.[13] Later, in December 2016, the US government added actions causing election interference to the list of malicious cyber activities after its intelligence community found evidence of actors linked to the Russian government interfering in the presidential elections.[14]
According to the Center for a New American Security tracker, the US Treasury Department announced 311 cyber-related sanctions from 2012 to 2021.[15] Most of these sanctions focused on the US’s known adversaries: Russia (141); Iran (112); and North Korea (18). The exception was when the US sanctioned in June 2020 six Nigerian nationals who, in their private capacity, had defrauded US nationals through cybercrimes.[16] Table 1 lists select significant US sanctions. Recent US sanctions have also targeted cybercriminal elements like Chatex and SUEX OTC, the virtual currency exchanges which facilitated ransomware payments.[17],[18]
Table 1: Significant US Cyber-sanctions (2015-2021)
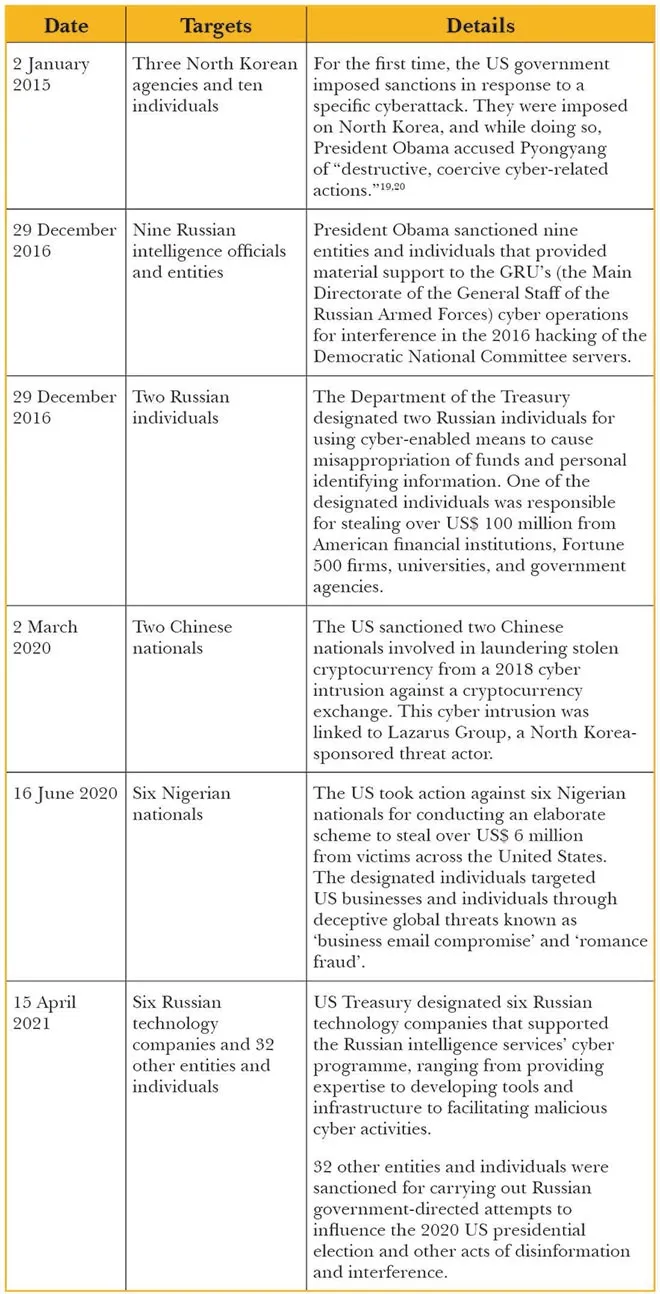
Source: Author’s own, using various open sources[/caption]
Sanctions can also serve as a protective tool for the states to increase their resilience to repeated cyber sabotage by curtailing the adversaries’ access to the required technologies.[19] This view rests on the belief that critical technologies augment the adversaries’ capability to execute cyber sabotage. Therefore, states can use sanctions to deny the adversary those very technologies. In April 2021, the US added the Russian technology sector to its cyber-sanctions regime, precisely seeking this.[20]
Despite the steps mentioned above, the US government agencies have faced challenges in implementing the cyber-sanctions regime, particularly in attributing the cyberattacks to specific threat actors and establishing their linkages with foreign government agencies.
Logistical challenges notwithstanding, the US has steadfastly expanded the scope of activities included under cyber-sanctions. Following the Obama administration’s lead, the US under then President Donald Trump escalated the use of sanctions in August 2017, when it enacted the Countering America’s Adversaries Through Sanctions Act (CAATSA). This act called for, among others, the implementation of sanctions on Russia for undermining US cybersecurity.[21] Washington would later bring a new sanctions executive order, in April 2021, providing additional powers to US government agencies to target harmful cyber activities by the Russian government and its interference in elections. It also extended restrictions on US banks’ dealings with Russian sovereign debt and authorised the US government to impose sanctions on Russian tech companies working with the Russian government.
Many allies have since emulated the US practice of cyber-sanctions. Across the Atlantic Ocean, the frequency of cyberattacks and hacking had forced a rethinking amongst the European countries to step up the EU’s response. In June 2017, the EU ministers of foreign affairs endorsed the development of a framework for a joint EU diplomatic response to malicious cyber activities, termed the “Cyber Diplomacy Toolbox.”[22] Its objective was to develop “signalling and reactive capacities” by the EU and its member states to influence the behaviour of potential aggressors.[23]
Two years later, in May 2019, the EU Council adopted the “Framework for a Joint EU Diplomatic Response to Malicious Cyber Activities,” allowing the organisation to impose targeted restrictive measures to deter and respond to cyberattacks.[24] The Council implemented this measure for the first time in July 2020 when it imposed restrictive measures against six individuals and three entities responsible for or involved in various cyberattacks, including the WannaCry, NotPetya, and Operation Cloud Hopper attacks and the attack against the Organization for the Prohibition of Chemical Weapons.[25]
The United Kingdom, too, after its exit from the EU in January 2020 put in place a mechanism called “The Cyber (Sanctions) (EU Exit) Regulations 2020”[26] that focuses on financial sanctions. As of May 2021, the UK has designated 16 individuals and six entities from North Korea, China, and Russia as targets of assets freeze.[27] Meanwhile, Australia inaugurated its cyber regime in December 2021, calling it a “thematic autonomous sanctions regime in relation to significant cyber incidents.”[28] The Australian regime covers both financial sanctions and travel bans. However, its Consolidated List of all persons and entities subject to targeted financial sanctions under Australian sanctions law does not mention any Chinese national or entity for malicious cyber activities.[29]
Among the US allies, the exception is Canada. Ottawa has a comprehensive autonomous sanctions regime, except it does not cover malicious cyber activities.[30] However, it has supported other like-minded partners’ measures like the EU’s cyber-sanctions listings.[31] Canada has also attributed specific cyberattacks to their perpetrators. For instance, in 2018, along with the US and Europe, it highlighted the role of the Chinese Ministry of State Security in the breach of several Managed Service Providers and third-party vendors.[32]
It is relevant to note that while Russia and China have retaliated against the general sanctions imposed by the West by imposing counter-sanctions, they have not followed a similar practice in retaliation to the West’s cyber-sanctions. Their response has instead been to insulate themselves from the West’s coercive actions.[33]
The Question of Efficacy
There are two dimensions in examining the efficacy of cyber-sanctions: their impact on the ability of bad actors to engage in malicious behaviour, and the challenges encountered in implementing these sanctions.
Empirical evidence suggests that current forms of cyber-sanctions have had little deterrent effect on the malicious behaviour of their target countries. For instance, the US sanctions on Russian intelligence officials and hacker groups have only generated additional cyberattacks on US computer networks. Likewise, repeated cyber-sanctions against North Korea have only emboldened its government to expand its targets over the years to include cryptocurrency exchanges and investment firms.[34]
The inability of cyber-sanctions to modify the behaviour of the targeted states reflects the trend observed in the case of general sanctions. It also points to the motivations of the malicious actors who will persist in offensive cyber actions if those actions align with their national interests and geopolitical objectives. For example, North Korea has repeatedly committed cyber heists by targeting banks and other financial institutions to refill its treasury and compensate for the assets freeze implemented as part of the United Nations (UN) sanctions.[35] This is even more true in the case of non-state actors, who are well aware of the consequences of their actions and, therefore, would have eschewed those services and activities targeted by the sanctions. Thus, they persist in executing malicious cyber activities.
To be sure, cyber-sanctions have affected targeted countries like Russia in one crucial respect: They have adversely affected the ability of the Russian digital and technology sector to conduct business as many of their clients and business partners have been sanctioned.[36] This impact, coupled with the specific technology-related sanctions imposed by the West after Russia’s Ukraine invasion, implies that the Russian tech companies have been losing out on commercial connections and contracts.[37] Businesses that are dependent on exports or foreign suppliers have particularly suffered.[38] The West’s cyber-sanctions have demonstrated ‘weaponised interdependence’ by leveraging its lead in technology supply chains and global financial architecture for strategic advantage.[39]
Moreover, for the West, sanctions have also highlighted the malicious activities of bad actors, thereby casting aspersions on their credibility. Again, while this may not impact the malicious behaviour itself, sanctions have served as a valuable instrument for Western policymakers to continually highlight the cyber threat stemming from its adversaries and the linkages between proxy actors like hacking groups, and state actors. In this context, sanctions have effectively exposed the Lazarus hacking group’s intimate connections with the North Korean state.[40]
Finally, to be successful, cyber-sanctions require a whole ecosystem approach, i.e., collaboration with other stakeholders such as financial institutions and other private sector elements. This is primarily for monitoring compliance and information sharing on potential sanctions regime violations. Western companies have generally adhered to both primary and secondary sanctions, despite multiple challenges like lack of clarity on sanctions rules, difficulties in payment mechanisms, and counter-sanctions from Russia and China.[41] However, since the Ukraine conflict began in February 2022, this has become a far more significant challenge for the companies given the severity of the latest Western sanctions, which seek to deny high-technology items and everyday industrial products to Russia.[42] On this count, therefore, both the US and EU will have to do more to on-board their businesses to ensure the latter’s compliance.[43]
Problem of Attribution
Effective implementation of cyber-sanctions crucially depends on the question of attribution—whether there is evidence to attribute a particular malicious cyber activity to a specific threat actor. Attribution is difficult because the malicious traffic is usually routed through multiple servers in different countries, making it difficult to determine the actual location of a computer. Moreover, identifying the location is not the same as finding out who the real perpetrator is—the computer could have been operated remotely.[44] Often, threat actors also use “The Onion Router” technology to anonymise their internet traffic.
It takes a combination of technical evidence, legal scrutiny, and political will to attribute a cyberattack to a specific perpetrator. Moreover, the evidence drawn for ascertaining attribution often relies upon classified technical capabilities. Those capabilities can become useless for future use or vulnerable to exposure once the evidence is brought into the public domain.[45] These dynamics weigh heavily when states ponder the question of attribution.[46] Leveraging these complexities, threat actors can conceal the origin of their actions. This has impacted the sanctioning country’s ability to punish the perpetrators and respond to cyberattacks.
However, the United States for instance, has developed significantly advanced technical forensic capabilities that can attribute an attack. Some experts therefore argue that the question is more of how long it will take to attribute a cyberattack, rather than if it can be done at all.[47]
To be sure, the question of attribution still remains nettlesome for the EU, where differences in member states’ technical and intelligence capabilities have hampered the effective implementation of its cyber-sanctions regime.[48] The EU also has persistent difficulties in evolving a classified information-sharing mechanism on cybersecurity issues among the member states, given the differences in legal practices, varied threat perceptions, and other operational reasons.[49] As pointed out by European cybersecurity expert Stefan Soesanto, classified intelligence sharing among the EU on malicious cyber activities occurs either by accident or by a proactive approach of an individual intelligence agency to seek relevant information.[50]
The issue of attribution is particularly complicated when it involves allies. For example, whistle-blower Edward Snowden in 2013 revealed that the US National Security Agency (NSA) regularly spies on its European allies and their commercial entities.[51] In one case, NSA was found to have monitored the mobile phone of then German Chancellor Angela Merkel. In another case, it urged its German counterpart to spy on technology company Siemens for suspected contacts with the Russian secret service.[52] These examples show that even allies choose to conduct offensive cyber operations against one other, in line with their respective national security considerations. The victim state may not want to attribute the attack to an ally, particularly if that ally happens to be the United States of America.
Relevance for India
Over the years, India’s cyber-threat canvas has become complicated with the growing maleficence from China and Pakistan. Their attacks have become far more penetrating and advanced, as evident from the Chinese state-sponsored hackers’ repeated breaches of the Indian power sector and Pakistan-origin malware ‘ReverseRat 2.0’ that targeted Indian government officials in 2021 to extract sensitive data.[53],[54] According to the Indian Computer Emergency Response Team (CERT-In), it handled 1,402,809 security incidents in 2021, as against 1,158,208 incidents in 2020 (see Figure 1).[55] Similarly, there was a 51-percent increase in ransomware incidents between 2021 and the first half of 2022.[56] This heightened cyber risk landscape threatens India’s core security interests and undoes whatever achievements the country has scored in the digital domain, including the greater use of digital payments and various technological innovations.
While India has reinforced its cyber defences, the persistence of malicious cyber activities calls for greater proactiveness to build a cyber-deterrence posture.
Figure 1: Cybersecurity Incidents Handled by CERT-In
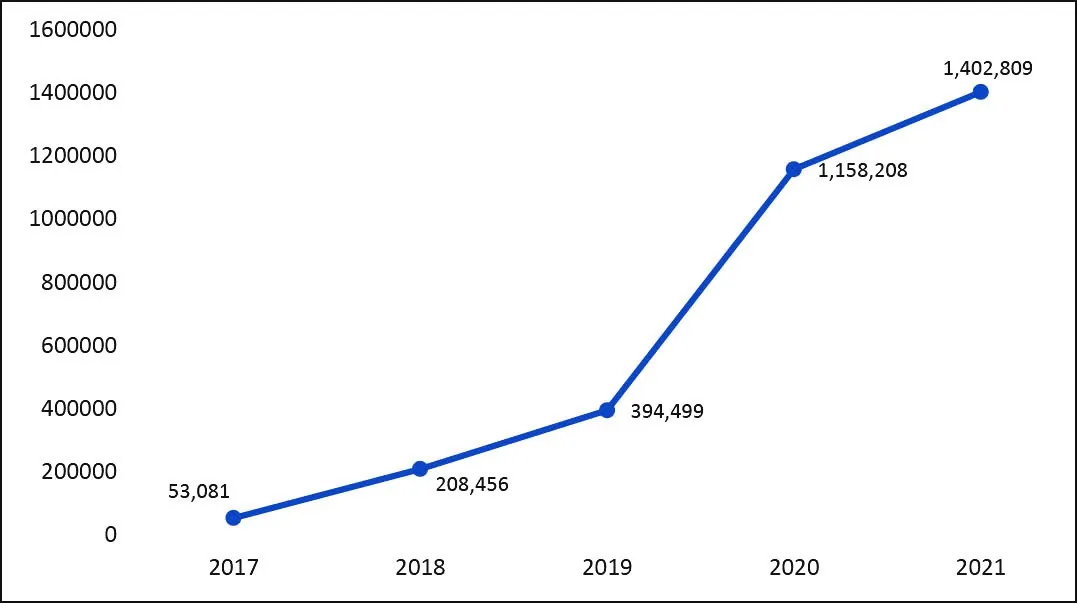
Source: Author’s own, using data from CERT-In’s annual reports
According to American political scientist Joseph Nye Jr., cyber-deterrence and dissuasion can be achieved through four means: the threat of punishment (retaliatory offensive actions); denial by defence (hardening cyber defences); entanglement (leveraging interdependence to avoid harms); and normative taboos (codes for responsible behaviour in cyberspace).[57] The West’s cyber-sanctions typically become part of the ‘threat of punishment,’ whereby it has sought to punish its adversaries for malicious cyber activities and ensure accountability. In this context, given their extensive use, the question is whether the tool of cyber-sanctions holds relevance for India.
India has repeatedly called upon the UN to develop norms for responsible state behaviour in cyberspace or evolve a common understanding among the member states, including on concepts such as cyber sovereignty, deterrence, and attacks.[58] Speaking at the UN Security Council’s open debate in June 2021, then Foreign Secretary Harsh Shringla, without naming Pakistan and China, highlighted that “some States are leveraging their expertise in cyberspace to achieve their political and security-related objectives and indulge in contemporary forms of cross-border terrorism.”[59]
New Delhi has also flagged attribution and legality of cyberattacks as critical dimensions in stabilising cyberspace.[60] Indian diplomats contend that while international law applies to cyberspace, it is inadequate to tackle the pressing issues of attribution, violation of sovereignty, and the threshold for invoking the right to self-defence.[61] Specifically, New Delhi has supported the ‘right to self-defence’ against state-sponsored cyberattacks.[62]
This assertion of the ‘right to self-defence’ is significant as it demonstrates the Indian government’s resolute approach to cybersecurity. As per the existing international legal principles, a state is only permitted to execute defensive actions in the case of an “armed attack,” which means the use of force must reach a certain threshold (deaths and/or damage or destruction of property).[63] However, as has been seen repeatedly in multiple instances of cyberattacks on India, such a threshold has not been crossed yet by the cyber adversaries, i.e., these cyberattacks have so far not assumed the form of kinetic and crippling cyberattacks.[64] In such a scenario, it is unlikely that India will resort to military measures. Sanctions can therefore be explored as a potential tool under the ‘right to self-defence’ against cyberattacks from its adversaries.
India has never supported the West’s autonomous/unilateral sanctions imposed outside the UN system, and it has been entangled in the West’s sanctions regime and the impact of secondary sanctions through CAATSA. However, India has recently begun exploring its version of sanctions—restrictive trade, commercial and technological measures in the interest of national security—in the aftermath of the February 2019 Lethpora terrorist attack and border stand-off with China and the June 2020 Galwan Valley clash. Following these incidents, India withdrew the ‘Most Favoured Nation’ status from Pakistan, banned Chinese apps, and instituted restrictive measures against Chinese investment in India.[65],[66],[67] Additionally, New Delhi excluded Chinese telecom companies from participating in the 5G network trials in the country.[68] Cyber-sanctions can therefore be considered as a more formal variation of this coercive strategy.
Policy Considerations for Utilising Cyber-Sanctions
In considering cyber-sanctions as a relevant tool to tackle adversaries, New Delhi must deliberate upon certain crucial aspects (see Table 2).
Table 2: Merits and Disadvantages of Cyber-sanctions as an Official Strategy
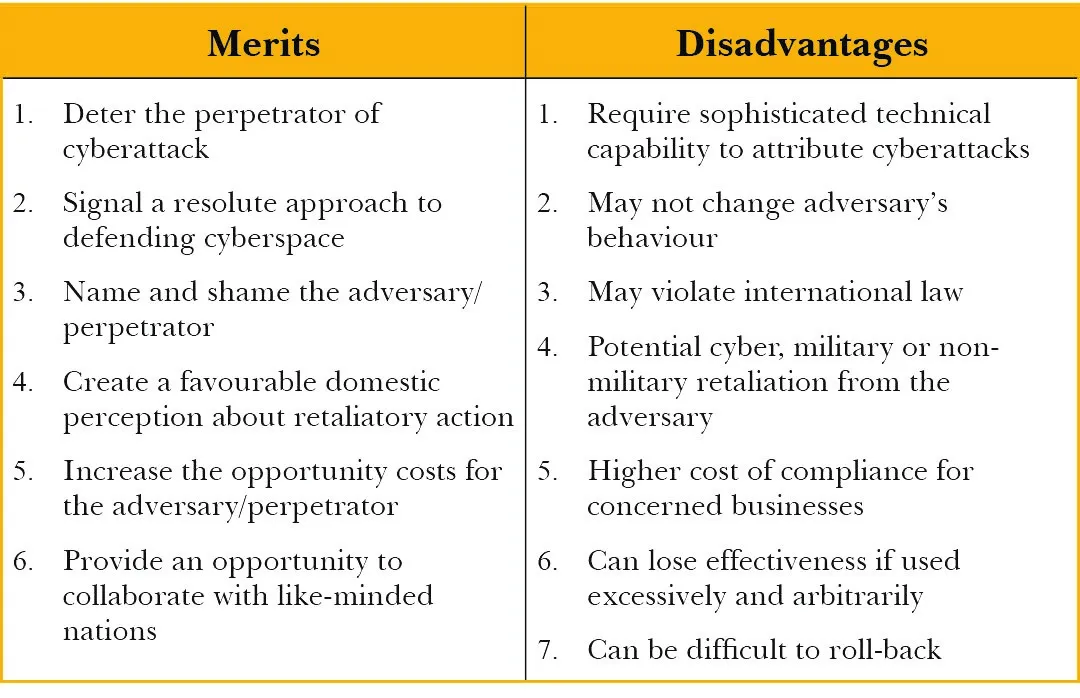
Source: Author’s own
First, Indian policymakers will need to define the purpose for which they will consider using cyber-sanctions: coercion (to deter the adversary and change its behaviour); denial (to impose costs on them by curtailing their access to the Indian market or tech sector); and/or as a symbolic measure (signalling the intent, name and shame the perpetrators of cyberattacks by designating them and exposing linkages between the state and proxy actors). Defining these aims is important for the efficient use of the sanctions instrument.[69] India will also need to be cognisant of the possible retaliatory measures like counter-sanctions from those sanctioned and more aggressive malicious cyber activities, and consider that autonomous cyber-sanctions may violate international law.[70]
Second, before India considers cyber-sanctions, it will need to put in place enabling domestic mechanisms like the Office of Foreign Assets Control in the US, a body within the Department of the Treasury that enforces economic and trade sanctions against the designated individuals and entities.[71] Creating such a body within the Indian setup will require setting a clear policy or law on sanctions and other restrictive measures and on what grounds they can be invoked.[72] Perhaps the National Cyber Security Coordinator’s office located within the National Security Council Secretariat can initiate an inter-agency consultation to debate the pros and cons of formalising a sanctions policy. The much-delayed National Cyber Security Strategy can be used to discuss the larger issue of cyber-deterrence and dissuasion.[73]
Third, as discussed briefly earlier, attribution is at the heart of cyber-sanctions. An examination of India’s track record on this count reveals that India is averse to attributing cyberattacks to its adversaries, particularly China, save for two occasions. First, in 2010, then National Security Advisor, MK Narayanan, admitted Chinese attempts to hack into the computer network in the Prime Minister’s Office.[74] Then, a decade later, in October 2020, Maharashtra’s Energy Minister hinted at the possible role of Chinese malware in disrupting Mumbai’s electricity supply.[75] However, enough technical, and anecdotal evidence suggests Chinese and Pakistani involvement in cyberattacks against India. Therefore, a key element of the potential cyber-sanctions strategy will require India to start outlining technical evidence to attribute cyberattacks to their perpetrators (state-sponsored or otherwise).[76] This will require working with the private sector cybersecurity community, which has begun to present such technical evidence. More importantly, India will need to consider the costs of such attribution, as it has live border disputes with China and Pakistan.
To mitigate such costs, it may be expedient to work with like-minded countries that can be partners in bringing accountability. These need not just include Quad members (Australia, Japan and the United States) and the European partners but also other countries that have fallen victim to China’s cyber maleficence such as Vietnam, Singapore, and Taiwan. India can coordinate positions with them on attribution and other related aspects.
Finally, as seen in the experience of other countries, cyber-sanctions cannot work independently and rather must be part of a broader strategy to tackle and counter malicious cyber activities. India is now hardening its cyber defences and undertaking offensive cyber operations.[77] While there are capacity and technical challenges in executing these measures, they must be combined to shape a cyber-deterrence strategy for India, learning from the experience of other cyber powers while remaining anchored in the country’s understanding of tackling cyber threats.[78] More importantly, as seen in the case of the West, relying too heavily on sanctions can diminish their efficacy. Therefore, the use of cyber-sanctions must be deliberate and selective.
Conclusion
The recent sanctions on Russia for its invasion of Ukraine indicate that the United States and its allies intend to ensure that its adversaries pay a cost for committing adversarial actions against them. Sanctions will play a critical role in tackling malicious cyber activities and will increasingly form part of a bouquet of coercive measures like technology export control regimes and trade restrictions.
The polarisation among the great powers and the lack of progress on global cyber cooperation connotes that affected states will resort to punitive measures such as cyber-sanctions to protect their cyberspace and national security. India will need to pay attention to these emerging trends to design its own cyber posture.
Sameer Patil is a Senior Fellow at ORF’s Strategic Studies Programme and has previously served in the National Security Council Secretariat.
(The author thanks Trisha Ray, Ambika Khanna, Kartik Bommakanti, Arindrajit Basu, and Virpratap Vikram Singh for their comments on an earlier draft of this paper.)
Endnotes
[a] These sanctions are enforced through enabling domestic legislation and broadly fall in the categories of sectoral and targeted sanctions. These sanctions include travel bans, asset freezes, restrictions on financial and commercial transactions, and curbs on the operations of technology companies.
[b] This brief defines the Western world to mean North America and Europe.
[1] Center for Strategic & International Studies, “Significant Cyber Incidents”.
[2] María Vásquez Callo-Müller and Iryna Bogdanova, “What Is the Role of Unilateral Cyber Sanctions in the Context of the Global Cybersecurity Law-Making?,” Völkerrechtsblog, May 10, 2022.
[3] Lesley Wroughton and Megha Rajagopalan, “Internet outage seen in North Korea amid U.S. hacking dispute,” Reuters, December 23, 2014.
[4] TOI Staff, “Israel behind cyberattack that caused ‘total disarray’ at Iran port – report,” The Times of Israel, May 19, 2020.
[5] Sameer Patil, Securing India in the Cyber Era (London and New York: Routledge, 2021, pp. 8.
[6] Terri Moon Cronk, “Iraq Progresses in ISIL Fight, Key Extremist Confirmed Dead,” DoD News, August 28, 2015.
[7] Israel Defense Forces (@IDF), “CLEARED FOR RELEASE: We thwarted an attempted Hamas cyber offensive against Israeli targets. Following our successful cyber defensive operation, we targeted a building where the Hamas cyber operatives work. HamasCyberHQ.exe has been removed,” Twitter Tweet, May 5, 2019.
[8] US Department of the Treasury, “Treasury Designates Iranian Ministry of Intelligence and Security for Human Rights Abuses and Support for Terrorism,” February 16, 2012.
[9] Andrea Peterson, “The Sony Pictures hack, explained,” The Washington Post, December 18, 2014.
[10] Lisa Richwine, “Cyber attack could cost Sony studio as much as $100 million”, Reuters, December 10, 2014.
[11] US Department of the Treasury, “Treasury Imposes Sanctions Against the Government of The Democratic People’s Republic Of Korea,” January 2, 2015.
[12] US Department of the State, “Cyber Sanctions”.
[13] The White House, “Executive Order – “Blocking the Property of Certain Persons Engaging in Significant Malicious Cyber-Enabled Activities,” April 1, 2015.
[14] The White House, “FACT SHEET: Actions in Response to Russian Malicious Cyber Activity and Harassment,” December 29, 2016.
[15] Jason Bartlett and Megan Ophel, “Sanctions by the Numbers: Spotlight on Cyber Sanctions”, Center for a New American Security, May 4, 2021.
[16] US Department of the Treasury, “Treasury Sanctions Nigerian Cyber Actors for Targeting U.S. Businesses and Individuals”, June 16, 2020.
[17] US Department of the Treasury, “Publication of Updated Ransomware Advisory; Cyber-related Designation”, September 21, 2021.
[18] US Department of the Treasury, “Treasury Continues to Counter Ransomware as Part of Whole-of-Government Effort; Sanctions Ransomware Operators and Virtual Currency Exchange”, November 8, 2021.
[19] Arindrajit Basu, Google Meet interview, May 16, 2020.
[20] US Department of State, “Holding Russia To Account, “April 15, 2021, https://www.state.gov/holding-russia-to-account/.
[21] US Department of the Treasury, “‘Countering America’s Adversaries Through Sanctions Act,” January 3, 2017, https://home.treasury.gov/system/files/126/hr3364_pl115-44.pdf.
[22] Council of the European Union, “Draft Council Conclusions on a Framework for a Joint EU Diplomatic
Response to Malicious Cyber Activities (“Cyber Diplomacy Toolbox”)- Adoption,” June 7, 2017, https://ccdcoe.org/uploads/2018/11/EU-170607-CyberDiplomacyToolbox-1.pdf.
[23] Erica Moret and Patryk Pawlak, “The EU Cyber Diplomacy Toolbox: towards a cyber sanctions regime?,” European Union Institute for Security Studies, 2017, https://www.jstor.org/stable/pdf/resrep06815.pdf.
[24] Council of the European Union, “Cyber-attacks: Council is now able to impose sanctions,” May 17, 2019, https://www.consilium.europa.eu/en/press/press-releases/2019/05/17/cyber-attacks-council-is-now-able-to-impose-sanctions/.
[25] Council of the European Union, “Amending Decision (CFSP) 2019/797 concerning restrictive measures against cyber-attacks threatening the Union or its Member States,” July 30, 2020, https://eur-lex.europa.eu/legal-content/EN/TXT/HTML/?uri=CELEX:32020D1127&from=EN.
[26] “The Cyber (Sanctions) (EU Exit) Regulations 2020,” Legislation.gov.uk, June 17, 2020, https://www.legislation.gov.uk/uksi/2020/597.
[27] Office of Financial Sanctions Implementation, HM Treasury, “Consolidated List of Financial Sanctions Targets in the UK,” May 27, 2022, https://assets.publishing.service.gov.uk/government/uploads/system/uploads/attachment_data/file/1079301/Cyber.pdf.
[28] Department of Foreign Affairs and Trade, Australian Government, “Significant cyber incidents sanctions regime,” https://www.dfat.gov.au/international-relations/security/sanctions/sanctions-regimes/significant-cyber-incidents-sanctions-regime.
[29] Department of Foreign Affairs and Trade, Australian Government, “Consolidated List,” https://www.dfat.gov.au/sites/default/files/regulation8_consolidated.xls.
[30] Government of Canada, “Current sanctions imposed by Canada,” March 19, 2021, https://www.international.gc.ca/world-monde/international_relations-relations_internationales/sanctions/current-actuelles.aspx?lang=eng.
[31] Global Affairs Canada, “Canada welcomes European Union’s announcement of new cyber sanctions listings,” July 30, 2020, https://www.canada.ca/en/global-affairs/news/2020/07/canada-welcomes-european-unions-announcement-of-new-cyber-sanctions-listings.html.
[32] Communications Security Establishment, “Canada and Allies Identify China as Responsible for Cyber-Compromise,” December 12, 2018, https://cse-cst.gc.ca/en/information-and-resources/announcements/canada-and-allies-identify-china-responsible-cyber.
[33] Caitríona Heinl “Debating the Tech Sanctions on Russia: Is ‘Splinternet’ Upon Us?,” Observer Research Foundation, April 26, 2022, https://www.orfonline.org/expert-speak/debating-the-tech-sanctions-on-russia/.
[34] United Nations Security Council, “Letter dated 25 February 2022 from the Panel of Experts established pursuant to resolution 1874 (2009) addressed to the President of the Security Council,” March 1, 2022, https://www.securitycouncilreport.org/atf/cf/%7B65BFCF9B-6D27-4E9C-8CD3-CF6E4FF96FF9%7D/N2225209.pdf.
[35] Bruce Klingner, “North Korean Cyberattacks: A Dangerous and Evolving Threat,” The Heritage Foundation, September 2, 2021, https://www.heritage.org/asia/report/north-korean-cyberattacks-dangerous-and-evolving-threat.
[36] Ivan Timofeev, Zoom interview, May 20, 2022.
[37] Arjun Gargeyas, “The effect of tech sanctions on the Russian economy,” Hindustan Times, March 16, 2022, https://www.hindustantimes.com/opinion/the-effect-of-tech-sanctions-on-the-russian-economy-101647423272681.html.
[38] Ivan Timofeev, “Sanctions Against Russia: A Look into 2021,” Russian International Affairs Council, Report 65/2021, March 11, 2021, https://russiancouncil.ru/papers/Sanctions2021-Report65-En.pdf.
[39] Farrell and Newman, “Weaponized Interdependence: How Global Economic Networks Shape State Coercion”, International Security 44, No. 1 (2019), https://doi.org/10.1162/isec_a_00351.
[40] US Department of the Treasury, “Treasury Sanctions North Korean State-Sponsored Malicious Cyber Groups,” September 3, 2019, https://home.treasury.gov/news/press-releases/sm774.
[41] Bruce Love, “Companies caught in EU-US sanctions crossfire”, Financial Times, January 30, 2020, https://www.ft.com/content/97a75318-16a8-11ea-b869-0971bffac109.
[42] Ivan Timofeev, Zoom interview, May 20, 2022.
[43] Christopher Burgess, “Internet sanctions against Russia pose risks, challenges for businesses,” CSO, March 22, 2022, https://www.csoonline.com/article/3654157/internet-sanctions-against-russia-pose-risks-challenges-for-businesses.html.
[44] P. W. Singer, and Allan Friedman, Cybersecurity and Cyberwar: What everyone needs to know (New York: Oxford University Press, 2014), pp. 72.
[45] Joseph S. Nye Jr, “Deterrence and Dissuasion in Cyberspace,” International Security 41 (2016/17) no. 3: 51.
[46] Thomas Rid and Ben Buchanan, “Attributing Cyber Attacks”, The Journal of Strategic Studies 38 (2014), no. 1-2: 4–37.
[47] Manuel Fischer, “The Concept of Deterrence and Its Applicability in the Cyber Domain,” Connections 18 (2019), no. 1/2: 69-92.
[48] Annegret Bendiek and Matthias Schulze, “Attribution: A Major Challenge for EU Cyber Sanctions,” Stiftung Wissenschaft und Politik Paper 11, December 2021, https://www.swp-berlin.org/en/publication/attribution-a-major-challenge-for-eu-cyber-sanctions.
[49] Stefan Soesanto, “After a Year of Silence, Are EU Cyber Sanctions Dead?,” Lawfare, October 26, 2021, https://www.lawfareblog.com/after-year-silence-are-eu-cyber-sanctions-dead.
[50] Soesanto, “After a Year of Silence, Are EU Cyber Sanctions Dead?”
[51] Spiegel Staff, “Intelligence Scandal Puts Merkel in Tight Place,” Spiegel International, May 4, 2015, https://www.spiegel.de/international/germany/bnd-intelligence-scandal-puts-merkel-in-tight-place-a-1031944.html.
[52] Spiegel Staff, “Intelligence Scandal Puts Merkel in Tight Place,” Spiegel International, May 4, 2015, https://www.spiegel.de/international/germany/bnd-intelligence-scandal-puts-merkel-in-tight-place-a-1031944.html.
[53] Insikt Group, “Continued Targeting of Indian Power Grid Assets by Chinese State-Sponsored Activity Group,” Recorded Future Blog, posted April 6, 2022, https://www.recordedfuture.com/continued-targeting-of-indian-power-grid-assets/.
[54] Black Lotus Labs, “ReverseRat Reemerges With A (Night)Fury New Campaign And New Developments, Same Familiar Side-Actor,” Lumen Blog, posted August 11, 2021, https://blog.lumen.com/reverserat-reemerges-with-a-nightfury-new-campaign-and-new-developments-same-familiar-side-actor/.
[55] CERT-In Annual Reports of 2021 and 2022, https://www.cert-in.org.in/.
[56] CERT-In, “India Ransomware Report for H1-2022,” https://www.cert-in.org.in/.
[57] Nye Jr., “Deterrence and Dissuasion in Cyberspace,”: 54—62.
[58] Ministry of External Affairs, Government of India, “Statement at the Organisational Session of the Open-Ended Working Group (OEW) on Developments in the Field of Information and Telecommunications in the Context of International Security,” June 3, 2019, http://meaindia.nic.in/cdgeneva/?8251?000.
[59] Ministry of External Affairs, Government of India, “Foreign Secretary’s Statement at the UN Security Council Open Debate on “Maintenance of International Peace and Security: Cyber Security,” June 29, 2021.
[60] Patil, Securing India in the Cyber Era, pp. 68.
[61] Patil, Securing India in the Cyber Era, pp. 68.
[62] Hannes Ebert, “Hacked IT superpower: how India secures its cyberspace as a rising digital democracy,” India Review 19, no. 4 (2020): 376-413.
[63] Manuel Fischer, “The Concept of Deterrence and Its Applicability in the Cyber Domain,”: 85.
[64] Kartik Bommakanti, “India and cyberspace: Balance between offence and defence,” Observer Research Foundation, June 18, 2021, https://www.orfonline.org/expert-speak/india-and-cyberspace-balance-between-offence-and-defence/.
[65] Press Information Bureau, Government of India, “Suspension of LoC Trade between J&K and PoJK,” April 18, 2019, https://pib.gov.in/PressReleseDetail.aspx?PRID=1570898.
[66] Press Information Bureau, Government of India, “Government Bans 59 mobile apps which are prejudicial to sovereignty and integrity of India, defence of India, security of state and public order,” June 29, 2020, https://pib.gov.in/PressReleseDetailm.aspx?PRID=1635206.
[67] Press Information Bureau, Government of India, “Investment from Land Border Sharing Countries,” March 23, 2022, https://pib.gov.in/PressReleaseIframePage.aspx?PRID=1808806.
[68] Anushree Fadnavis, “India doesn’t name Huawei among participants in 5G trials,” Reuters, May 4, 2021, https://www.reuters.com/technology/india-doesnt-name-huawei-among-participants-5g-trials-2021-05-04/.
[69] Moret and Pawlak, “The EU Cyber Diplomacy Toolbox: towards a cyber sanctions regime?”
[70] http://opiniojuris.org/2022/01/24/unilateral-cyber-sanctions-and-global-cybersecurity-law-making/
[71] US Department of the Treasury, “Office of Foreign Assets Control - Sanctions Programs and Information”.
[72] Ambika Khanna, Google Meet interview, May 11, 2022.
[73] PTI, “Government to unveil national cyber security strategy soon: National Cyber Security Coordinator,” The Hindu, July 3, 2021.
[74] Express News Service, “Chinese hacked PMO computers, says Narayanan,” The Indian Express, January 19, 2010.
[75] “Sabotage suspected in Mumbai power outage: Nitin Raut, Energy minister”, The Economic Times, October 14, 2020.
[76] Sameer Patil and Kishika Mahajan, “Expanding Chinese cyber-espionage threat against India,” Observer Research Foundation, April 18, 2022.
[77] Gunjan Chawla, “Does India have offensive cyber capabilities?,” The CCG Blog, July 10, 2020.
[78] Deependra Singh Hooda, “Towards a Cyber Deterrence Strategy for India,” Delhi Policy Group, Policy Brief VI, no. 19 (July 2021).
The views expressed above belong to the author(s). ORF research and analyses now available on Telegram! Click here to access our curated content — blogs, longforms and interviews.

 PDF Download
PDF Download






 PREV
PREV


